The Mobile Network Battlefield in Ukraine – Part 3
This blog is co-authored by Cathal Mc Daid and Rowland Corr
In this multi-part blog series on the Mobile Battleground in Ukraine, we first covered the many security and resilience steps that the Ukrainian Mobile Operator community took to defend their mobile networks. In the 2nd part we discussed what the actual implication of these steps have been on the course of the 2022 Russian Invasion of Ukraine so far. Having paused for a number of weeks to review the latest developments, we now have our third and final blog entry in the series.
This blog has two main sections:
- the framing of what we have observed to date in our understanding of what is ‘cyberwarfare’,
- What we expect to be the next developments in the ‘Mobile Network Battlefield’
As part of this, this blog will also cover two rarely-discussed separatist Russian-controlled mobile operators, active on the territory of Ukraine since the last invasion in 2014. Click here if you want to go directly to this section.
Cyberwar, or not?
As we covered in our first blog, in general, this conflict has not featured the expected impact of cyberattacks, compared to what many IT-security commentators would have expected to occur in a large-scale war. Since we issued our first blog, there have been some reported incidents of serious attacks on telecom and energy facilities, but by and large they have been repelled successfully. While keeping in mind that not all attacks are publicly reported, and information on others will no doubt come out over time, it seems that the actual impact these reported IT attacks have had on the course of the war is limited.
On the other hand, as we have shown in our blogs so far, the use of mobile networks has played a huge part in:
- marshalling international support for Ukraine,
- impacting Russian forces’ communications and therefore effectiveness, and
- allowing Ukrainian forces to receive information about Russian troop movements to execute attacks.
Therefore, it cannot be credibly said that new ‘cyber’ technologies are not playing a massive role in this conflict so far. How can we reconcile these two views?
One way is to go back to the more traditional, wider view of the Battlefield, and take the model of recognising the convergence of ‘cyber’ operations, with electronic warfare operations along with the wider world of Signals intelligence. Simply put, to understand the potential execution and use of cyber operations in a kinetic conflict, we need to look at the whole ‘spectrum’ of electromagnetic operations that it resides in. One way to represent this overlap, and the different functionality, is below.
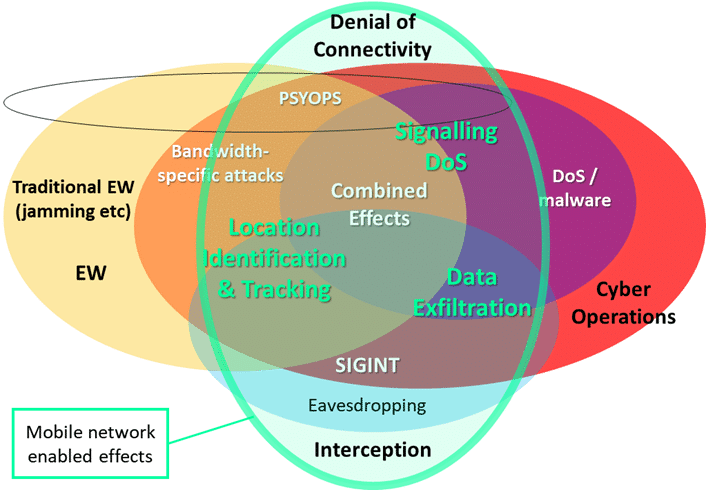
Figure 1: Converged view of EW, Cyber Operations and SIGINT. Modified version of Porche, et al (2013),as outlined here originally published from a CERDEC draft
By taking models like these as a guide, we can see that these IT attacks form only one part of the much greater arena where IT and mobile technologies are utilized and contested on the battlefield. This is not to say that analysing IT attacks on their own is not without value, but that it tends to be discussed in a way that does not consider activities in the wider wireless environment, and effectively ignores the wider EME (electromagnetic environment). In real-life, in Ukraine today, there is a digital war effort that revolves around the full integration of activities in the cyber and electromagnetic contexts by military as well as non-military actors. We are far from the first people to use this model of placing cyber activities in a wider EW and SIGINT sphere. As well as the article and book linked to above, a similar perspective has been taken by the UK Ministry of Defence (MOD) in what they term Cyber and Electromagnetic Activities (CEMA).
As well as being a more comprehensive, integrated and realistic view of the electronic battlefield, shifting focus from the conduct of cyberattacks to the wider contest allows us to show the importance of mobile connectivity as a force multiplier. This involves not only enhancing but also fundamentally enabling military operations across the spectrum of offensive and defensive action. From this perspective, actions in Ukraine have highlighted the battlefield utility of mobile network infrastructure in Electronic Warfare – understood as strategic use of the EME against an enemy in a military conflict – and its relationship with cyber action. As an example of this, actions on the battlefield in Ukraine – as described in detail in Parts 1 and 2 of this series – demonstrate what Kostyuk and Zhukov (2017) concluded to have been historically lacking in wartime ‘cyber’ action to date, namely an ability to “visibly affect” the actions of the enemy. One specific incident showing this was the Ukrainian discovery of the Russian forces’ recourse to using SIM-box equipment seemingly to sustain battlefield communications. This would have been compelled by Ukrainian operators’ blocking of Russian SIM registration from the outset of the invasion.
We will go into these concepts in more detail in a future blogpost. However, we believe that the course of this war has shown how the wartime use of IT-related capabilities should be gauged by how far they directly enable or enhance conventional warfighting, rather than focusing on the presence or absence of hacking attacks against this or that infrastructure. In other words, the question is one of integrated capabilities, not coincident activity.
The Future
While the above model is one way to show the use of mobile networks in the conflict to date, we can also look at the conflict so far to project forward. Especially, we will try to answer what are both the defending Ukrainian forces and the aggressor Russian forces likely to do in the mobile arena in the future?
Ukrainian Mobile Networks – More Resilience and Security
It can be no surprise that what we can expect for the Ukrainian mobile networks is a combination of what has happened in the past, that is – a continuation of Resilience and Security. This will also be shaped by where the war is expected to be fought in the foreseeable future – that is regionally in the east and south
We expect continuing Resilience and Security to be built into the Ukrainian mobile networks, in order to support the war effort. As well as the massive undertaking in rebuilding mobile infrastructure damaged by the war, some additional examples that have happened or been announced in the past few weeks since our last blogs are:
- The construction of new cell towers in western Ukraine to handle the additional load and capacity issues due to many IDPs moving there.
- The trialling and testing of an emergency Cell Broadcast system, this will allow authorities to issue an alert to mobiles in any region or cell nationally, in case of an air-raid or other form of attack.
- The trialling and use of Starlink satellite terminals as a backhaul method from celltowers in newly liberated areas, back to core switching points, via satellite links. This is especially useful where cable damage is extensive, and other backhaul methods may not be available.
- The use of directional, long range GSM antennae to provide and restore communications quickly in areas with no power to sustain the local existing cell towers
- The trialling of a SMS mechanism that will allow people in order to receive a text alert whether a member of family switches his mobile phone back on.
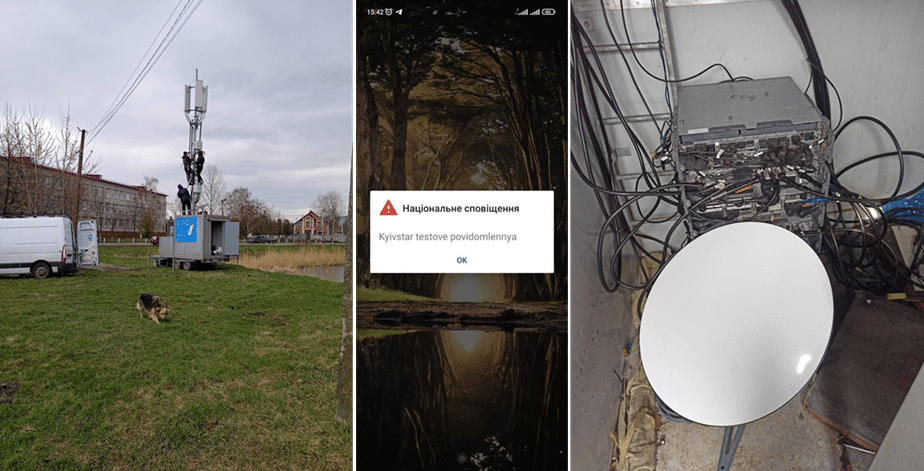
Figure 2: Pictures of: 1) Temporary Kyivstar Cell-tower being deployed, 2) Testing of Emergency Cell Broadcast system, 3) Starlink system functioning as a Vodafone Ukraine cell-tower backhaul
Many of these systems would normally take months to negotiate and integrate, so the speed in which they are being delivered and setup is impressive. We expect that additional improvements and innovations will continue to occur.
Russian Attempted Response – Separatist Mobile Operators
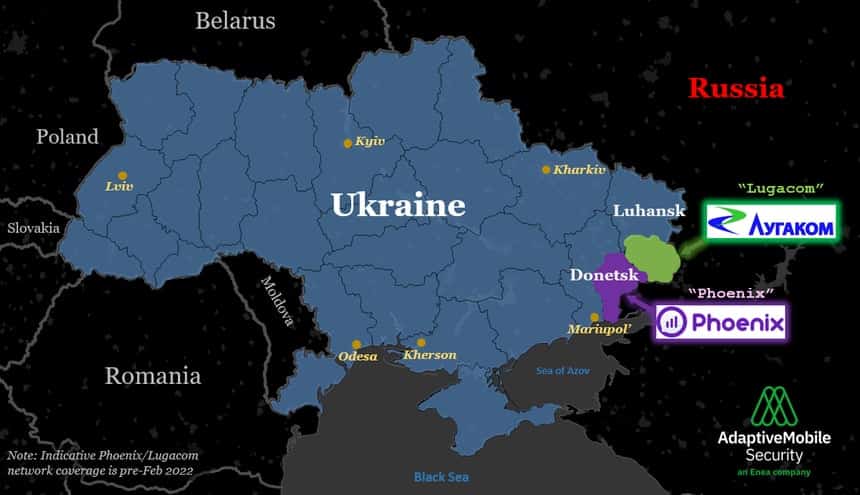
However, these improvements are not only occurring on the Ukrainian side. On the Russian side there are also moves to build up resilience and security. One of the most obvious and potentially impactful is the role and expansion of the little-known (proxy Russian) separatist Mobile Operators. While there are several Ukrainian Mobile operators, of which the main 3 are Kyivstar, Vodafone Ukraine and Lifecell, there also actually exist 2 separatist-run mobile operators which operate in the separatist held areas of the Donbas. These are:
- Phoenix (Феникс), sometimes spelt as Feniks, in separatist-held parts of Donetsk, and
- Lugacom (Лугаком), sometimes spelt as Lugakom, in separatist-held parts of Luhansk.
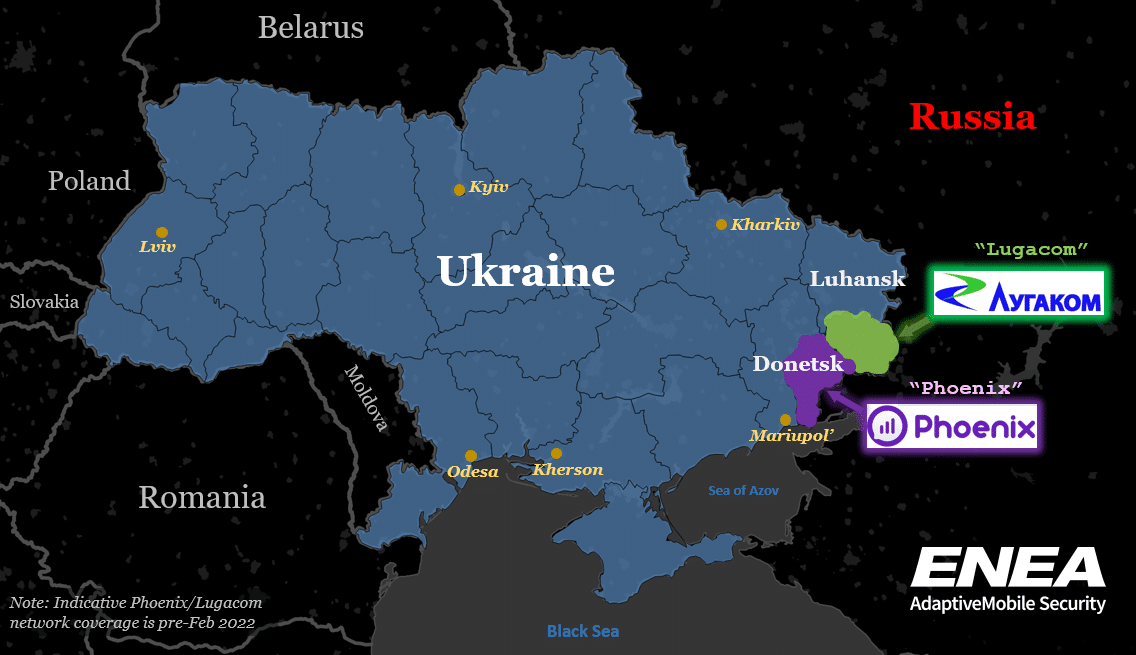
These have formed over time from seized Lifecell and Kyivstar equipment since the 2014 invasion, and have grown in subscriber numbers as those Ukrainian Mobile Operators were gradually pushed out from the region. The total number of subscribers for these operators is hard to quantify, but pre the 2022-invasion it was probably below 1.5 million. While they are nominally separate, they actually share the same Mobile Network Code (99), and a SIM from one can be used on the other network. In general, these separatist controlled operators are not licensed by the Ukrainian regulator – so are not regarded as legitimate – and phone calls to and from them cannot be made to subscribers of the licensed Ukrainian mobile operators, or to any other country generally other than Russia. This makes any phone containing a Lugacom or Phoenix SIM card only useful locally.
Since the 2022 invasion begun though, both separatist mobile operators have been expanding into newly overrun areas of Donetsk and Luhansk. This is done by reportedly erecting new base stations (cell towers) or attempting to re-use existing ones from the legitimate Ukrainian operators – if the separatists have the access and knowledge. We can speculate that this is being done in order to attempt to both incorporate the local population into these separatist administrative areas and to try to make it harder for Ukrainian authorities to easily monitor and intercept phone calls or track locations of Russian troops. The map below shows where new Lugacom/Phoenix coverage or work has been reported by these entities or other news media in the area. Due to the source of information (separatist media or the operators themselves), this must be taken with caution, and a reported working base station may be anything but. However, the map also shows OSINT front lines as a reference as of April 18th and the reports to now generally align well with the current situation on the ground in the region, occurring in Russian-seized territory somewhat back from the front lines.
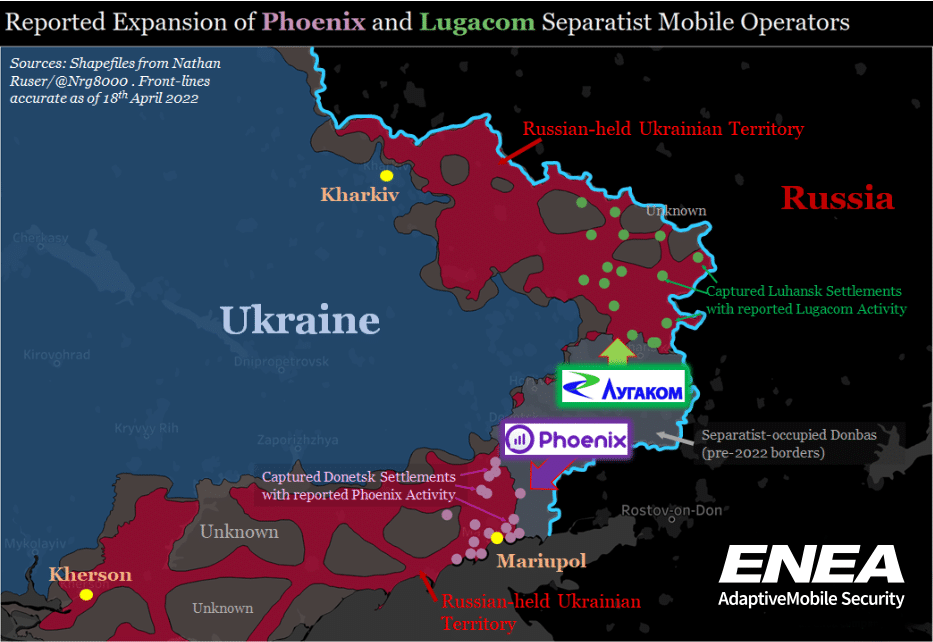
Figure 4: Villages or Settlements where the expansion of Phoenix (pink) and Lugacom (green) Basestations or equipment has been reported. Front lines as reported as of 18th April. Sources: Social Media, Phoenix, Lugacom. Frontlines shapefiles: Nathan Ruser
We can further analyse the proposed expansion of Phoenix in particular into the newly occupied territories by comparing its reported coverage maps on its website. By comparing its current purported coverage against the pre-2022 ceasefire lines we can see that it now claims to have 2G coverage in a large area of south-western Donetsk, along with patchy 3G coverage. Again, this information must be regarded as suspect but, interestingly, we can also see that Phoenix say they have deployed outside of Donetsk proper, in the settlement of Rozivka (Розівка), which is in Zaporizhzhya Oblast.
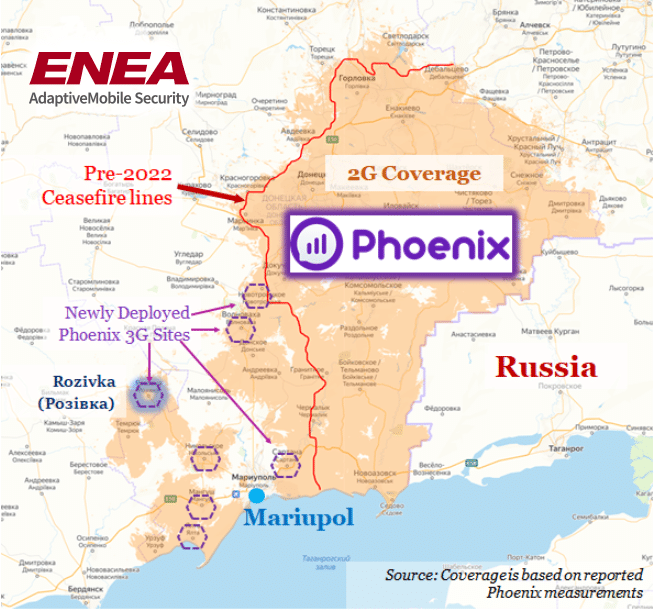
Figure 5: Reported recent coverage of separatist Phoenix Mobile Operator relative to pre-2022 ceasefire line. The expansion into Rozivka outside of Donetsk Oblast is shown as purple. Reported expansion 3G cells show as hexagons. Source: Phoenix
Outside of the Donbas, there other reports of further Russian mobile operator expansion, although in less detail than the Phoenix/Lugacom activity. Near the city of Kharkiv in the east, Ukrainian military intelligence reported that equipment from the Russian operator Megafon (МегаФон) has been installed. In the Kherson region in the south there have been local Ukrainian government reports of seized Ukrainian Operator equipment. This has been accompanied of reports on social media of cell towers with the same separatist Mobile Network Code (99) being detected in the Kherson region.
If these reports are confirmed, firstly this could mean that seized border areas of Russia/Ukraine in the east near Kharkiv would be planned to have direct Russian Mobile network coverage. If the service is run by Megafon this would be interesting as Megafon are the 2nd largest Russian Mobile Operator and have not reportedly been active so far in Ukraine – including in Crimea other than in a roaming mode. Generally, the Russian operators have avoided deploying in occupied regions of Ukraine likely due to the fear of sanctions. However, Megafon are licensed in Abkhazia and South Ossetia – two disputed regions of Georgia in the Caucasus. The reports of MNC 99 in the south are also interesting. If true, this means that we could expect an expansion of a separatist mobile operator into these areas in the south. Initially the purpose of this network may be to primarily assist Russian forces and other occupation personnel using Lugacom/Phoenix SIM cards, but a new branded Kherson or southern proxy mobile operator open to the captive civilian population may be formed if the occupation continues in these areas. This is likely to be setup along the same lines as Lugacom and Phoenix.
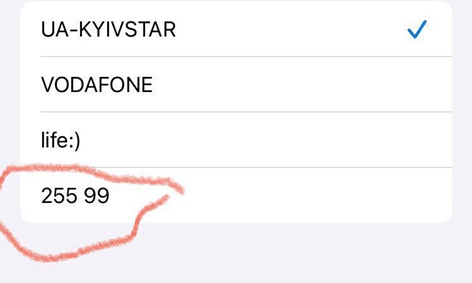
Figure 6: Reported Screenshot from social media of a 255 99 Mobile Operator reportedly broadcasting in Kherson region in the south. 255 is the Mobile Country Code (MCC) of Ukraine, and 99 is the unlicensed Mobile Network Code (MNC) that Phoenix and Lugacom have used in the Donbas.
As well as building up their own mobile networks, a side-effect of the capture of specific Ukrainian mobile network equipment is that it could allow the Russians to execute internal core network attacks on the Ukrainian mobile operators. As we covered in our previous white paper in 2014 the capture of Ukrtelcom network equipment in the Crimea by Russian troops was used to launch telephony DoS attack on member of the Ukrainian Rada. Recently, it seems like this internal core network attack vector has indeed been attempted, as in the last week there have been reports of SS7 attacks being launched from captured Ukrainian network infrastructure. More can be expected.
Overall, it can be said that if the Russian/Separatist mobile networks expand successfully then their use -and the use of uncontrolled internal links – could help negate some of the advantage that the Ukrainian state has sustained in denying connectivity (i.e. EME access) to Russian forces on the ‘mobile battlefield’.
Evaluation of Outcomes
However – like in many parts of the war – Russia may find that it is as hard establishing supremacy on the mobile battlefield as it is on the conventional field, even if it is concentrating on the Donbas. There are two specific pieces of information we can give showing this:
- Firstly, the separatist mobile operators themselves, have a long history of outages and issues, and this is not likely to improve, if anything it may get worse. There have been multiple reports of outages over time, and recently, there has been reports* of a multiple day outage in Lugacom, which is forcing it to work in a ‘limited’ mode. In fact it is difficult to tell if the outage has indeed been corrected. One stated reason in the separatist press for these current outages is that individuals needed for maintenance are unavailable due to mobilisation. This seems plausible given current conditions and past history, but it also seems at odds due to the mobile networks’ strategic importance especially at this time. It is also unusual to happen at the same time as Lugacom/Phoenix personnel are seemingly available to physically expand the separatist mobile networks by co-opting or building new base stations. Whatever the reason for the outage, if does not bode well for the stability of these networks. In addition, separatist mobile operators will find it doubly hard to expand and maintain these expanded networks in the future due to the effect of sanctions on Russia. This will impact them in procuring replacement telecom equipment such as transmission systems and core network components.
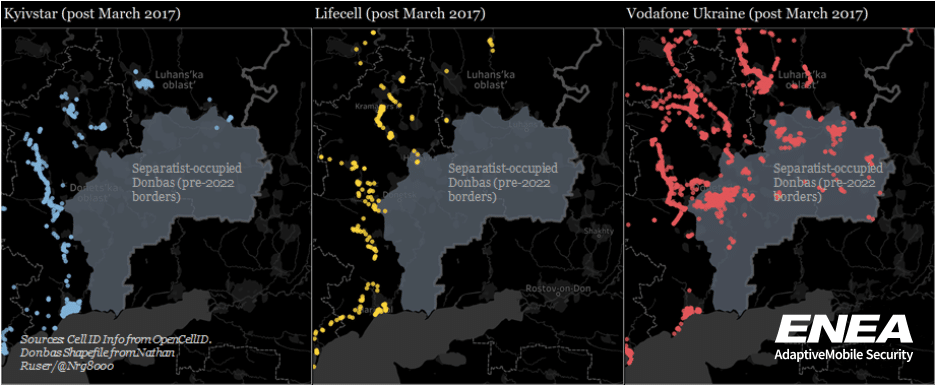
- Secondly, mobile connectivity via Ukrainian networks are even more reduced to Russian troops in the Donbas compared to other areas. Previously we had explained that Phoenix/Lugacom had partially built their networks from seized Kyivstar and Lifecell equipment, and these 2 operators no longer operated in the separatist-held Donbas. However, there has been a continuing legitimate presence of the 3rd Ukrainian Mobile Operator – Vodafone Ukraine – in the Donbas area right up until the war. This split in the Donbas can be viewed through reports of reported CellIDs in opensource databases (see diagram below). Since the start of the war though, separatist media has carried reports that Vodafone Ukraine is no longer available in the breakaway areas. While any reports from these areas needs to be treated cautiously, from our observations of international SS7 traffic from Ukraine – we also observed a change in the nature of the Vodafone Ukraine traffic from this general area. Namely that it seemed to have stopped. There are pros and cons to both sides for this development, however, from a defensive Ukrainian viewpoint, there are sound tactical reasons for why this would be beneficial. The obvious reason is it would completely deny the use of the Vodafone Ukraine network to Russian and separatist troops in this area
- Related to this, another very important reason for cutting off this area is it would prevent any possibility of these systems being used to launch internal attacks on the internal Ukrainian networks. It is obvious that this (the use of internal network connections to launch attacks) would be a tactic that the Ukrainian Mobile Community would have strongly investigated and plan to defend against. Evidence that it was anticipated is that the Ukrainian regulator had already issued strict and detailed instructions on what Communications providers should prepare for to prevent their telecom equipment is captured, and what to do if it is. As a result, we should expect the Ukrainian side to have planned to make defensive moves if telecom equipment fell into enemy hands during wartime.
The end result is that these Russian attempts to establish and use mobile communications in the combat areas are likely to run into a lot of difficulty, and so we predict that more problems will arise due to the non-availability of mobile networks to Russian forces.
Lastly, it should be realised that decisions of the operation of mobile networks in a war do not take place in a vacuum – the lives of the civilian population and their safety also have to be considered. Like many decisions in wartime, this can lead to difficult trade-offs. To give an example, as we covered in our first blog, inbound Russian and Belarusian subscriber roaming on Ukrainian networks are disabled. As well as stopping the use of these devices by Russian forces, it also improves Ukraine’s mobile network (SS7/Diameter) interconnect security profile. However, roaming in the other direction – Ukrainian subscribers to Russia is not completely blocked – even though this would also help Ukraine’s mobile security profile. The reason? One reason may be because so many people have been brought from Ukraine to Russia during the war against their will, and they may need help to escape. As a result some of the Ukrainian operators have made calls to embassies of friendly 3rd countries free (zero-rated), so these people have a chance to get help. If these outbound roamer Ukrainian connections were blocked – for a marginal mobile network security improvement, then calls and use of the phones by captured Ukrainian civilians would not be possible – for a far worse human impact.
Conclusion
In general, we can expect that both sides will try to build up the capacity and the utility of the mobile networks on their sides. There will continue to be outages and physical damage on the Ukrainian networks in the combat areas, but the Ukrainian networks have (unfortunately) gained a large amount of experience in overcoming them. One of the main dangers to the Ukrainian Mobile networks in the combat areas is the high risk of their equipment, in Russian over-run areas, being co-opted and used over time to establish Russian-controlled networks. This cannot happen overnight, it takes time and effort, especially given the reduced resources available to the Russians but as we have seen it has already begun in the captured territories. As well as the benefits to the occupation this gives to Russia, this captured equipment could be used to launch internal core networks attacks, and indeed it seems as this has been reported already. Careful monitoring and defences will be required here to control and prevent any ill-effects from such attacks.
The Mobile network battlefield has had a profound impact on the execution and course of the war so far in Ukraine, and we expect that to continue. This 3-part blog series has covered some of the major mobile network developments over the past few weeks, and what we can learn from them. One key outcome that has arisen is that the concept of ‘cyber’ warfare in this environment is – so far – different than what many expected, and in real life, and in real time, mobile communications have been at the heart of it. To date, the Ukrainian mobile community (Mobile Operators, Regulator and Security services) have managed to weather the initial attacks. In fact, more than that ,they have adapted and used their capabilities to greatly disadvantage the Russian invaders. A key part of that has been preparation prior to the invasion, co-ordination amongst the Ukrainian mobile community (and beyond), and the ability to quickly react and innovate when needed. While many observers have seen not just a poorer IT but also a poorer Russian EW performance than expected, the fact is an attacker must work in the overall CEMA (Cyber and Electromagnetic Activities) environment they the defender gives them. In this respect Russian forces have had to work in the mobile battlefield that the Ukrainian mobile community have set, although as we have shown there are strong signs that recently the Russian forces seeking to change it. Whether this will be successful remains to be seen. We expect in the new focused and critical conflict in the east and south that the mobile battlefield will continue to play a large part in its outcome.
If you wish to donate to Ukrainian charities supporting the communications needs of Ukrainian refugees, a specific charity assisting communications on the border is: Télécoms Sans Frontières (TSF)
*Update 03/08/2023 – original link of https://lug-info.com/news/svyaz-lugakom-rabotaet-v-ogranichennom-rezhime-iz-za-avarii-na-oborudovanii-minkomsvyaz was replaced