The Mobile Network Battlefield in Ukraine – Part 2
In our previous blog we covered the many security and resilience steps that the Ukrainian Mobile Operator community took to defend their mobile networks, in this next blog in this series we go deeper into what are the actual implication of these steps on the course of the 2022 Russian Invasion of Ukraine so far.
Impact on the War
The effect of all of the moves we covered in part 1, in both securing the mobile network, and expanding its utility to both civilian and military users has made a massive difference to the path of the war so far. For example:
The effect on morale and the international response
A functional mobile network, in which people can speak, text and message each other and those abroad has obvious morale improving implications, along with the ability to access the internet through mobile devices. But there are many examples that show the positive impact on morale. Specific examples range from the practical: such as the thousands of images of destroyed Russian vehicles from the field being uploaded by mobile phones, to the inspirational: such as President Zelenskyy’s Telegram message, recorded on his phone, on the day after the invasion begun saying he is alive and well in Kyiv. These arguably not only lead to a greater morale within the country, but – along with the immutably sadder images of the effects of the invasion on the Ukrainian civilian population – have also helped pave the way for military international aid, as well as the acceptance for international sanctions on Russia.

Left: Ukrainian soldier posing beside destroyed tank. Right: President Zelenskyy video in Kyiv recorded on February 25th. Source: Twitter, Telegram
The impact on the Russian invasion forces
The denial of much of the utility of the mobile network to invaders has helped shape this war. It is interesting to note, that unlike Ukraine, Georgia did not block inbound Russian mobile phone roamers when they were invaded by Russia in August 2008. In Georgia in 2008, Russian forces used the Georgian mobile networks for communications when their radio equipment during that invasion was not sufficient. This time, Russian forces, again facing radio issues, have also had to resort to using the invaded country’s mobile networks. However, due to the Russian inbound roamer blocking implemented by Ukraine, the only way they can be utilised is by using Ukrainian or other non-Russian/Belarusian SIM cards. Reports have surfaced of ‘clean Ukrainian SIMs’ being available for Chechen commanders, and presumably other members of the Russian armed forces, and in addition some (probably small number of) seized Ukrainian SIMs may be in use. These SIMs would be used to communicate between themselves and with Ukrainian individuals at times.
But these SIMs, being active on Ukrainian mobile networks, mean Russian forces have opened themselves up to call, voice and data interception at multiple points once known and identified. This is no doubt the source of multiple phone interception, including some of those that have attributed to have led to the deaths of 2 Russian Generals. In addition, if identified, these SIMs can have their location recorded using the mobile phone network, as the Chechen leader Kadyrov’s Russian mobile phone was reportedly checked to determine whether he entered Ukraine or not. The use of a SIMBox for call relaying as explained in our earlier blog is clearly a way to bypass interception – as calls inside the country will draw less attention – but its detection and ongoing search for other methods like this means that the utility of these networks to the Russian side is severely restrained.
The execution of the war
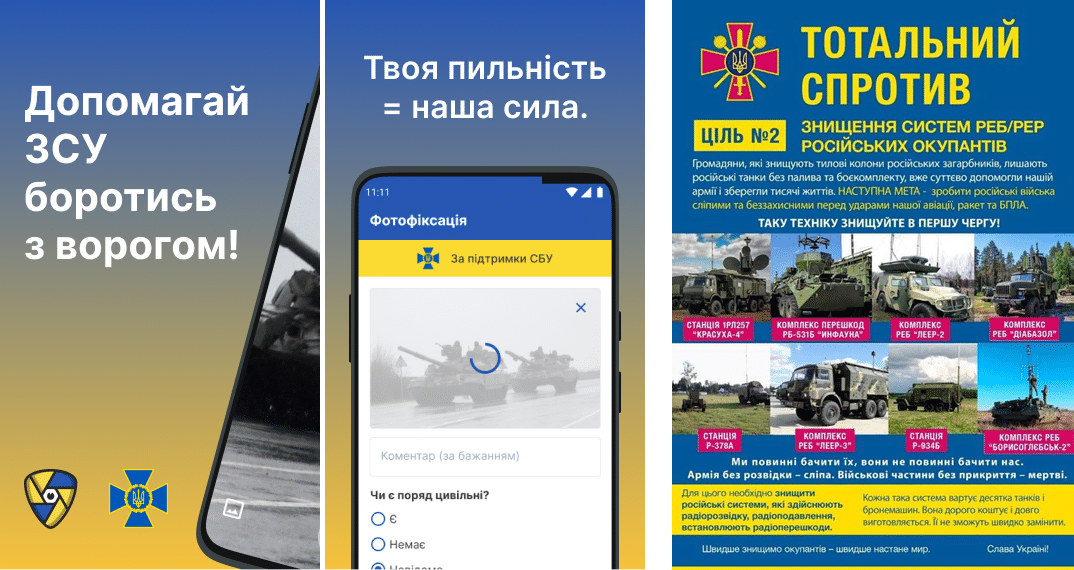
Mobile devices have had a myriad of uses within the war, from helping to take pictures of locations and damage, to being used to help guide drones – with other communication systems . One of the most innovative uses of the mobile networks, is the use of it in directly helping to take the war to the Russian forces. Specifically, the Ukrainian army has setup multiple formal methods in which that people could report the positions of Russian forces, these include a Telegram channel, a website and even an app called Bachu that uploads details once data connectivity has been re-established.
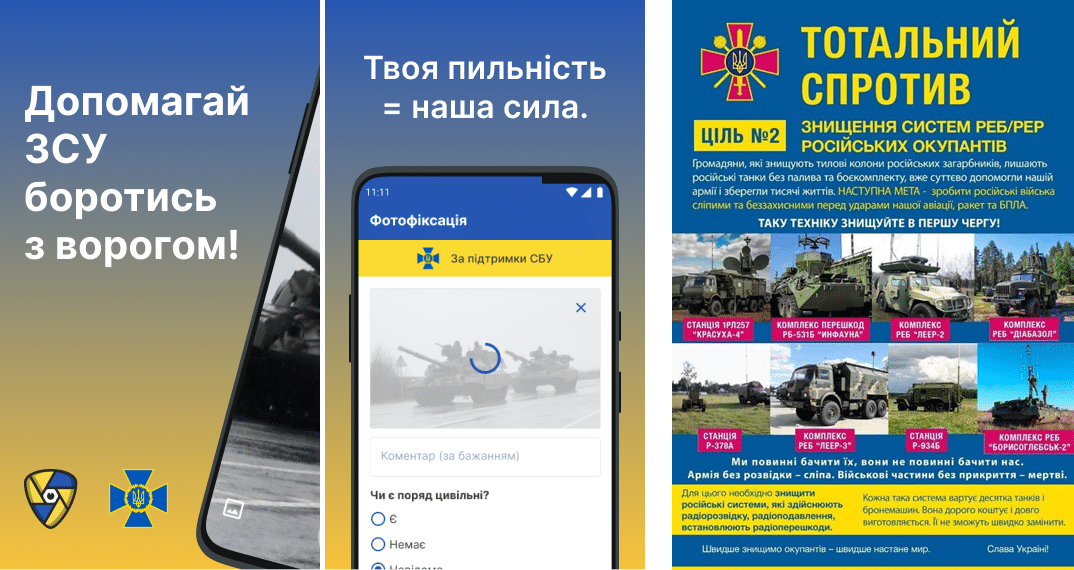
Left/Centre: Bachu App to report enemy movements, Right: Russian EW Systems to report/destroy
This is probably one key reason why National roaming was expanded in the Ukraine from the more ‘standard’ SMS and Voice sharing only in emergency announced on the 7th of March , to also cover a degree of mobile internet on the 12th of March. This “kill-chain crowd-sourcing” – helped and guided by the Ukrainian Ministry of Defense pushing out visual charts (such as Russian Electronic Warfare systems) of what is valuable to report/destroy – has probably been the first time that civilian input into military operations and what to target has been automated to such a degree. No doubt there have also been a myriad of informal ways that enemy positions have been communicated to Ukrainian commanders through sending of pictures or reports via Voice, SMS or messaging.
Preparation for the Fight
It must be kept in mind, that many of these changes could not have taken place over-night, that they are the culmination of months, and in some cases years of preparation. To give some example:
- National roaming had been suggested before, within Ukraine, it had been suggested as an option to overcome issues both in the Crimea and in the Donbass in 2014, due to some of the Ukrainian mobile operators having their equipment interfered with at the time, although it was not implemented then. Even before that time however, Ukraine has put in the necessary legal underpinning for national roaming, something many countries worldwide have not done. A legal underpinning is not enough though, as to implement national roaming there needs to be a co-ordinated agreement on many topics about how it could work, not least on billing flows and capacity constraints, and then the technical ability to implement it. It can have said to be a success though, because, in the 5 days after it was introduced over 1.3 million people used the service, with notable example being the employees of the captured Zaporizhzhia nuclear power plant, as well as the residents of Mariupol, where at the end, regardless of their phone subscription a single remaining Kyivstar cell tower was used by those residents in signal range to communicate.
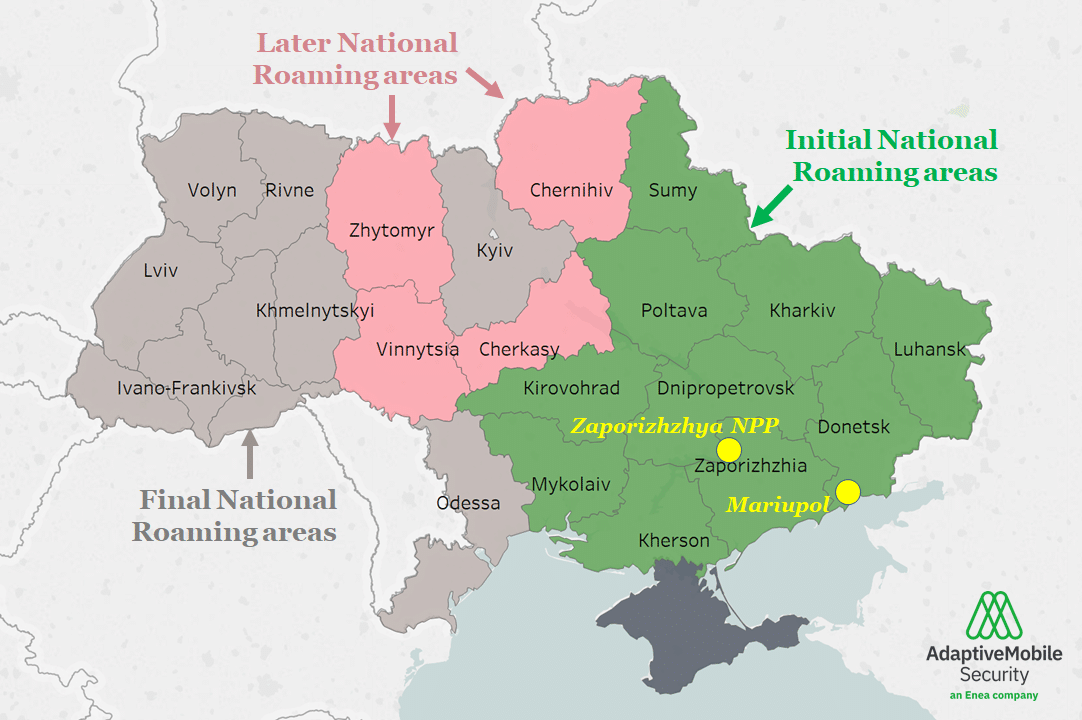
Map of Ukrainian areas (oblasts) where National Roaming was announced to be enabled initially (Green), and then to enabled later (Pink). Note: actual roll-out may have differed. Data source: Ukrainian Telecom Regulator (NKRZI)
- Another decision was the co-ordinated blocking of roaming for Belarusian and Russian mobile devices on the night of the 24th and 25th. In our paper covering Hybrid warfare we previously outlined tactics like this, where we stated: “Defensive examples could include the prevention of all roaming updates from hostile mobile network sources or links,,,” , but we also clearly state in our paper that: that plans needed to be put in place prior to any hostile action to allow such decisions and actions to be made, as these are complex implementations that need to be taken. The Ukrainian Mobile Operators clearly had these plans in place due to the fact that were able to make these quick decisions.
This last point is important due to the little known nature of how mobile networks work. We have previously reported how Russian-originated , potential state-level actors have used the SS7 (2G+3G) mobile interface for location tracking and interception of specific individuals. Also, in the past, Ukraine experienced SS7 location tracking and call interception at the start of the 2014 Donbass Invasion, and as we cover in our paper, Russian capabilities in this area is extensive. The blocking of inbound roaming means, that as well as Russian forces not being able to use their SIM cards, on the cybersecurity side this also means that the Ukrainian mobile operators can greatly reduce their ‘attack surface’ from Russian mobile SS7 and Diameter(4G) network sources. While Russian communications interception may still be possible along the frontlines using EW warfare assets such as the Leer3 complex, by making these pre-planned network changes, Ukraine can reduce the risk of interior, country-wide attacks which could have targeted a much wider range of individuals. Essentially Ukraine both increased the possibility it could intercept the mobile communications of Russian troops (by forcing them to use non-Russian SIMs), while conversely they can reduce the possibility that Russia could intercept Ukrainian mobile communications.
Finally, one unusual perspective that has been taken by some observers, in trying to explain why Ukrainian Mobile Networks were still functioning after several weeks of war, was to put it all down to decisions made by the Russian forces. This perspective has a side effect of assuming that the Ukrainian side had no agency in whether their own networks were still active. We believe that this viewpoint is fundamentally wrong, as the cadence and scope of the decisions made by the Ukrainian Mobile Operators, both before and after the Invasion – as well as their ongoing work to keep them active – show that they are clearly engaged in the fight to keep these networks alive.
However , as we have seen these Mobile Networks are more than simply alive, they are being used on a global and national level as a means to boost morale, obstruct the enemy and as a ‘force-multiplier’ in stopping the Invasion. Next week we will discuss the example of the wider impact of these Mobile Networks in our understanding of what is ‘cyberwarfare’ (a somewhat ambiguous and overused, yet underdeveloped term), as well as what we expect to the next developments in the ‘Mobile Network Battlefield’