Designated Attacker – Evolving SS7 Attack Tools
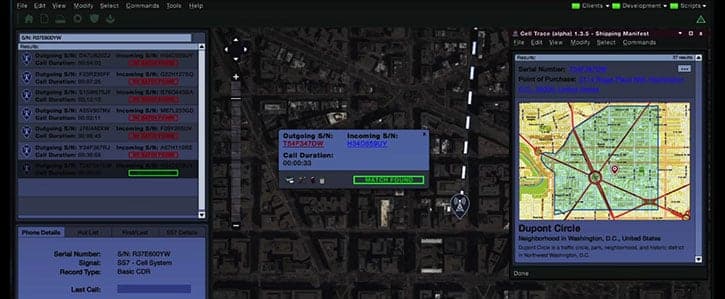
In the last episode “The Oath” of the Netflix series “Designated Survivor”, there is a need for an FBI agent to track down the location of a mobile phone. Their solution is to access the SS7 network, which as they describe as “the method that allows every cell tower to talk to other so your phone works anywhere in the world”

This description is broadly correct, although to be precise, strictly speaking celltowers do not use the ss7 network, they connect to core network elements that do. The method used in the TV series itself is a bit more dubious technically, the actual method that is used in the show seems to be the lookup of CDR files, which are billing files generated as the outcome of SS7 network activity, rather than directly ’hacking’ the SS7 core network. Regardless, using this approach, the agents are seemingly able to locate the device that made a call to the heroine of the series, and (somehow), they are then able to track down the shop at which the phone was bought it. While looking for complete or even partial technical accuracy in a TV series is not recommended, what it does show is how the awareness of mobile network security has made itself even into the mind of Hollywood script writers.
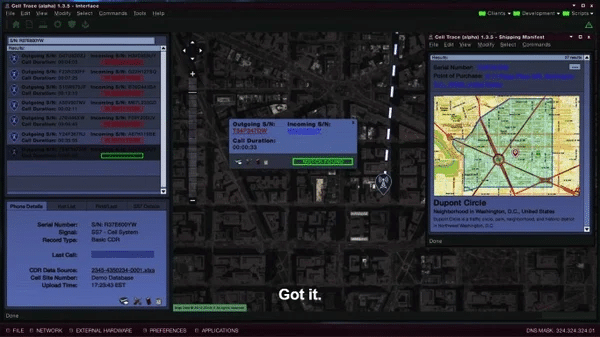
This also illustrated something that we have been aware of for a while, while there may be a perception that the SS7 network is easily abused, in reality, right now it isn’t. Unlike a TV show, it takes more than a few keystrokes to abuse the SS7 network, it takes expertise, money, and access. But from what we have seen, once attackers have all 3 they are making sophisticated use of SS7, because once you have this ability, you want to exploit it fully.
In general, there are probably 3 main classes of misuse of SS7 networks
- Anomalous, but not malicious traffic. This can be everything from malfunctioning nodes, attempting to send for all subscribers rather than their own, to unusual implementations of legitimate services, to anything else which is not known to be malicious. The skill here is in identifying this and making sense of what is malicious and what isn’t – not always easy to understand.
- Malicious attacks, up to a medium-level complexity. These are the more well-known location tracking, fraud and information harvesting attacks, and were the main type of attacks that operators encountered when they started to investigate SS7 security in depth. As time has gone on, the perception of ‘simple’ has risen in complexity to cover more and more types of attacks. These can normally be well defended against
- Malicious attacks, of advanced complexity. This is the type of attack that takes investigation to even identify in the first place, and once identified requires detailed understanding of what the attacker is trying to achieve and how, in order to build consistent defences against. These are the most advanced type of attacks they will increase in complexity as time goes on
We are actually seeing a progression over time (i.e. over the last 2 years), where some of the attackers who have access to the SS7 network have progressed to trying to use more and more sophisticated methods to achieve what they want, especially now that a large number of operators have begun to implement defences. One thing that helps these attackers are operators who just deploy standard, off the shelf Firewalls, or simply upgrade existing network equipment to block known malicious, medium-level complexity attacks. Without a dedicated security element, over time the determined attackers will try more advanced attacks and are able to find holes through the initial defences. Like a body trying to deploy antibiotics, without a sufficient and evolving defence over time the attackers will mutate and overwhelm the existing static defences.
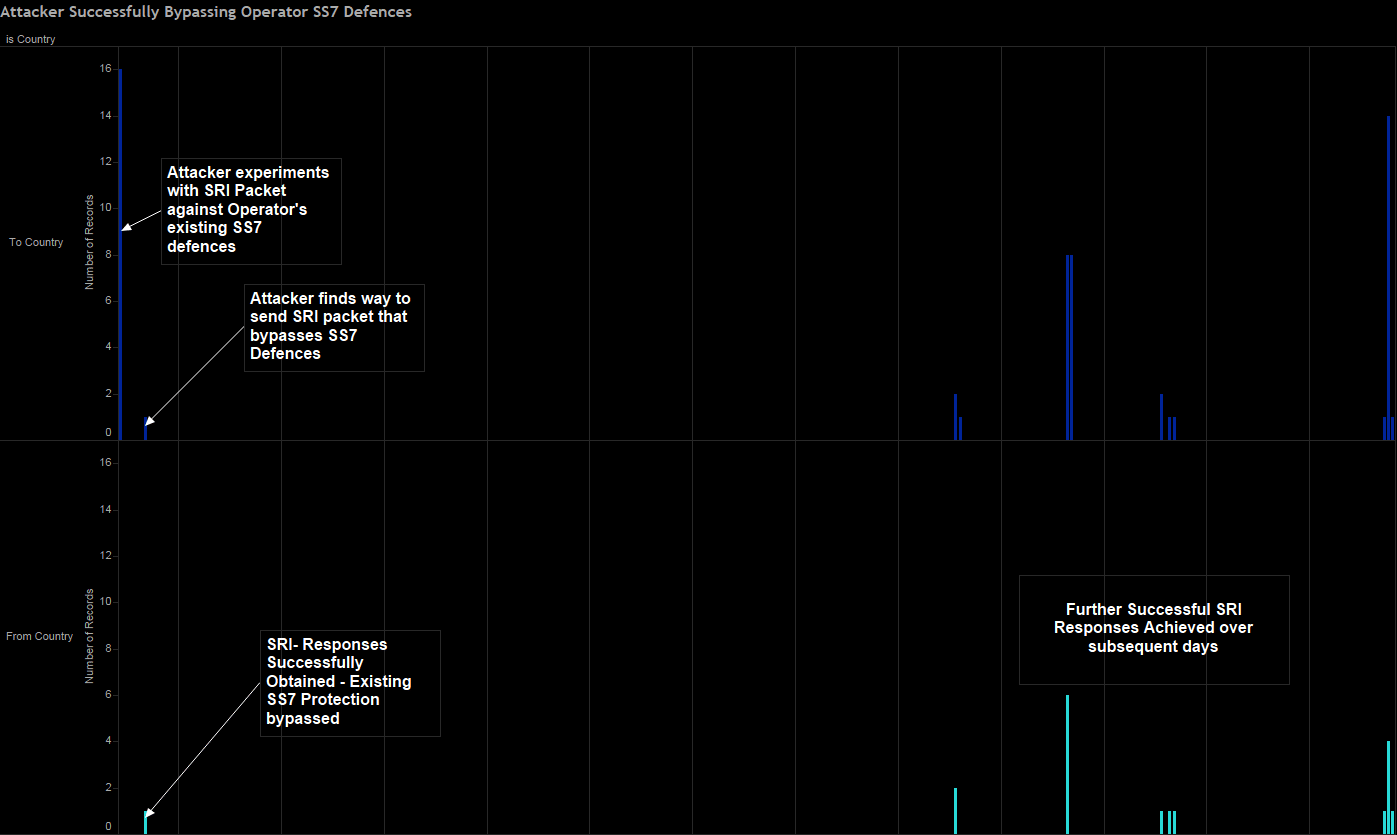
Diagram shows a recent recorded incident of where an attacker managed to penetrate an Operators SS7 defences with Send Routing Information (SRI) packets. These type of Packets can be used for both subscriber information harvesting, and as a precursor to further attacks
Surveillance, and interception of communications are big business, both in the past and even more so in the future. With recent reports and warnings from security agencies of information being shared over SMS there is a need to make sure that mobile networks are fully protected. Unlike what was shown in the Designated Survivor episode, it may not be as easy as a few clicks, for an attacker to get access to the SS7 network. But once they have access they will use it and it is only logical they will continue to improve their attacks and try to bypass any defences put in place so they can continue to get value from it. The key for Carriers who want to protect their networks and their subscribers is to start planning now, assume these (designated) attackers will be constantly testing and improving, and get ready to defend for the long-term.
You may also want to read our post on the Pegasus Project.