Profiling Russian Operators emerging in occupied Southern Ukraine
In our previous 3-part blog series, we covered many aspect of the use of Mobile Networks in the 2022 Russian Invasion of Ukraine. One particular area we covered was the expansion of the previously little-known Russian separatist mobile operators in the Donbass, and the potential emergence of new Russian separatist mobile operators in Southern Ukraine. Since then, the broad outlines of the Russian strategy in the telecom area have become clearer. In this blog, as part of our presentation at the VirusBulletin2022 conference, we give an update of these mobile networks developments and reveal new research that allows us to associate these new mobile operators with others under Russian control.
As we covered in the 3rd part of our 3 part blog series, there existed 2 separatist-run mobile operators which operate in the separatist held areas of the Donbas. These are:
- Phoenix (Феникс), sometimes spelt as Feniks, in separatist-held parts of Donetsk, and
- Lugacom (Лугаком), sometimes spelt as Lugakom, in separatist-held parts of Luhansk. It renamed itself MCS (МКС) in July 2022
These have formed over time from seized Ukrainian Lifecell and Kyivstar mobile operator equipment since the 2014 invasion, and have grown in subscriber numbers as those Ukrainian Mobile Operators were gradually pushed out from the region. While they are nominally separate, they actually use the Ukrainian Mobile Country Code (255), share the same Mobile Network Code (99), and a SIM from one can be used on the other network. In general, these separatist controlled operators are not licensed by the Ukrainian regulator – so are not regarded as legitimate.
We covered in our previous blog the expansion of these separatist mobile operators in newly occupied parts of Donetsk and Luhansk until the end of April. Since that time the following developments have occurred:
Phoenix
One major development, is that Phoenix has announced that it will switch from Ukrainian to Russian phone prefixes for its subscribers.. Previously Phoenix had self-allocated Ukrainian mobile phone numbers in the range +38071. Now, it is planned to move to a new Russian area-code of +7 949. This is a sign of the growing attempted ‘Russification’ of the region. However, this change is not altogether straightforward, and if the local authorities wish to go further and change the IMSI from a Ukrainian (255) to a Russian Mobile Country Code (250), they will probably need new SIM Cards – a difficult undertaking in the middle of a war.
Another major development is that the separatist mobile operator, according to its own coverage maps , has expanded beyond Donetsk oblast (region) , and into Russian-held parts of Zaporizhzhia and Kherson, although it seems more Zaporizhzhia-based so far. We observed an early sign of this in our blog from the end of April 2022 when Phoenix had reported they had set up coverage in the settlement of Rozivka (Розівка), which is in Zaporizhzhya oblast.
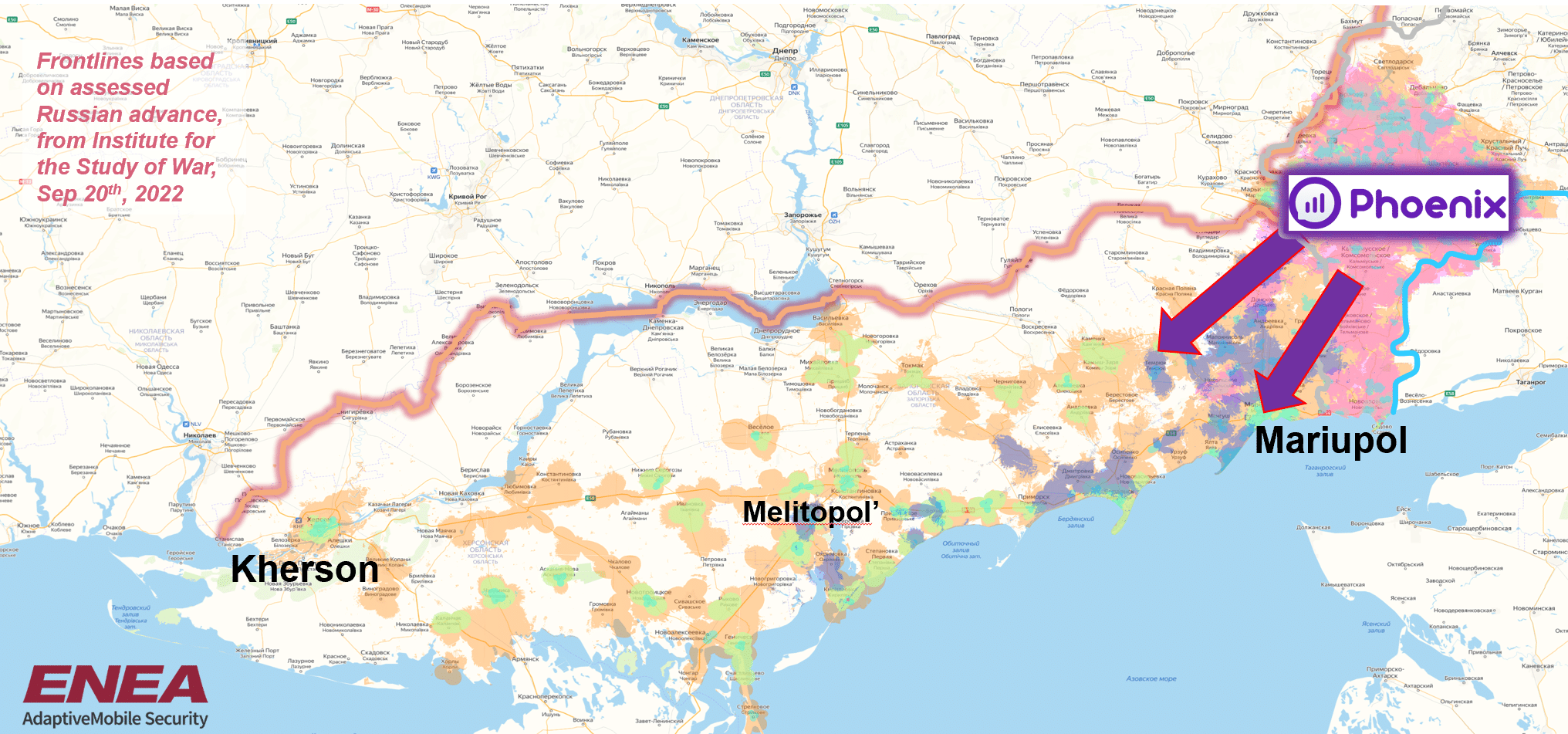
Network Expansion as reported by Phoenix. Frontlines as reported by ISW as of Sep 20th 2022
In these regions it uses a range of Radio communication technology – 2G, 3G and 4G, although the 4G radio frequencies it uses are normally in the lower ranges in the newly occupied territory (800MHz/900MHz). While we should not trust what these website reports when it comes to location – not least because coverage maps themselves are generated based on expected coverage, not from actual measurements. There have been reports on social media or elsewhere of this MCC+MNC being observed in occupied Southern Ukraine – as we also briefly covered in our last blog.
MCS (Lugacom)
MCS, as the new name of Lugacom, has also evolved and changed since we last analysed this in late April 2022. Like Phoenix, it is planned to move to a new Russian area-code of +7 959. Previously it had self-allocated Ukrainian mobile phone numbers in the range +38072. Again, this would be part of attempted ‘Russification’ of the region. Another obvious difference is the new name of the mobile division name, this was changed with little notice in July 2022 to MCS. The remaining Lugacom division is now a fixed-line/internet company. The rational for this name-change is not clear. It may be perhaps that the use of the prefix in Lugacom (Лугаком) was too closely associated with the name of the oblast of Luhansk/Lugansk (Ukrainian: Луганськ Russian: Луганск), and so for future expansion outside of Luhansk the name should be changed to improve its commercial attraction.
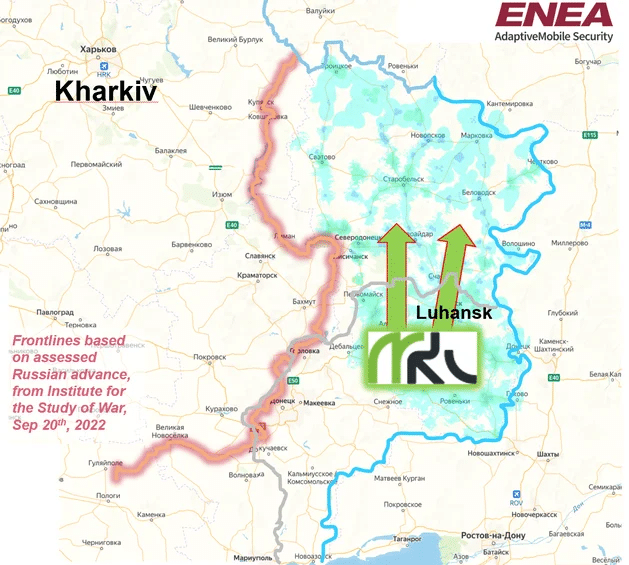
Network Coverage as reported by MCS. Frontlines as reported by ISW as of Sep 20th 2022
One surprising difference though, is that from its own reported coverage maps MCS has not expanded beyond occupied Luhansk, even when parts of the neighbouring region of Kharkiv was under Russian control. In fact, a different newly founded mobile operators – MirTelecom – setup mobile coverage in occupied Kharkiv , more on this later. This may be because of failures on MCS’s part in the past , possibly bringing its competence into question, or some internal manoeuvring within Russian decision makers to exclude it. However, the recent recapture by Ukrainian forces of occupied parts of the Kharkiv area means this whole conversation is now academic.
+7 Telecom
Since our last blog, the existence of two new Mobile Operators in Southern Russia has come to light . The first of these is +7 Telecom , which looks to have become active at the end of May 2022. Unlike Phoenix and MCS, the numbering systems used indicate they are designed to be Russian from the start. It uses a previously unallocated Russian area code of +7 990, and the MCC-MNC is 250-96, where 250 is the Russian Mobile Country Code (MCC). According to their coverage maps they have 2G and 4G coverage in Zaporizhzhia and Kherson. Again, we cannot confirm that all reported coverage matches reality, but there are social media and other media reports of these networks being encountered within occupied southern Ukraine.
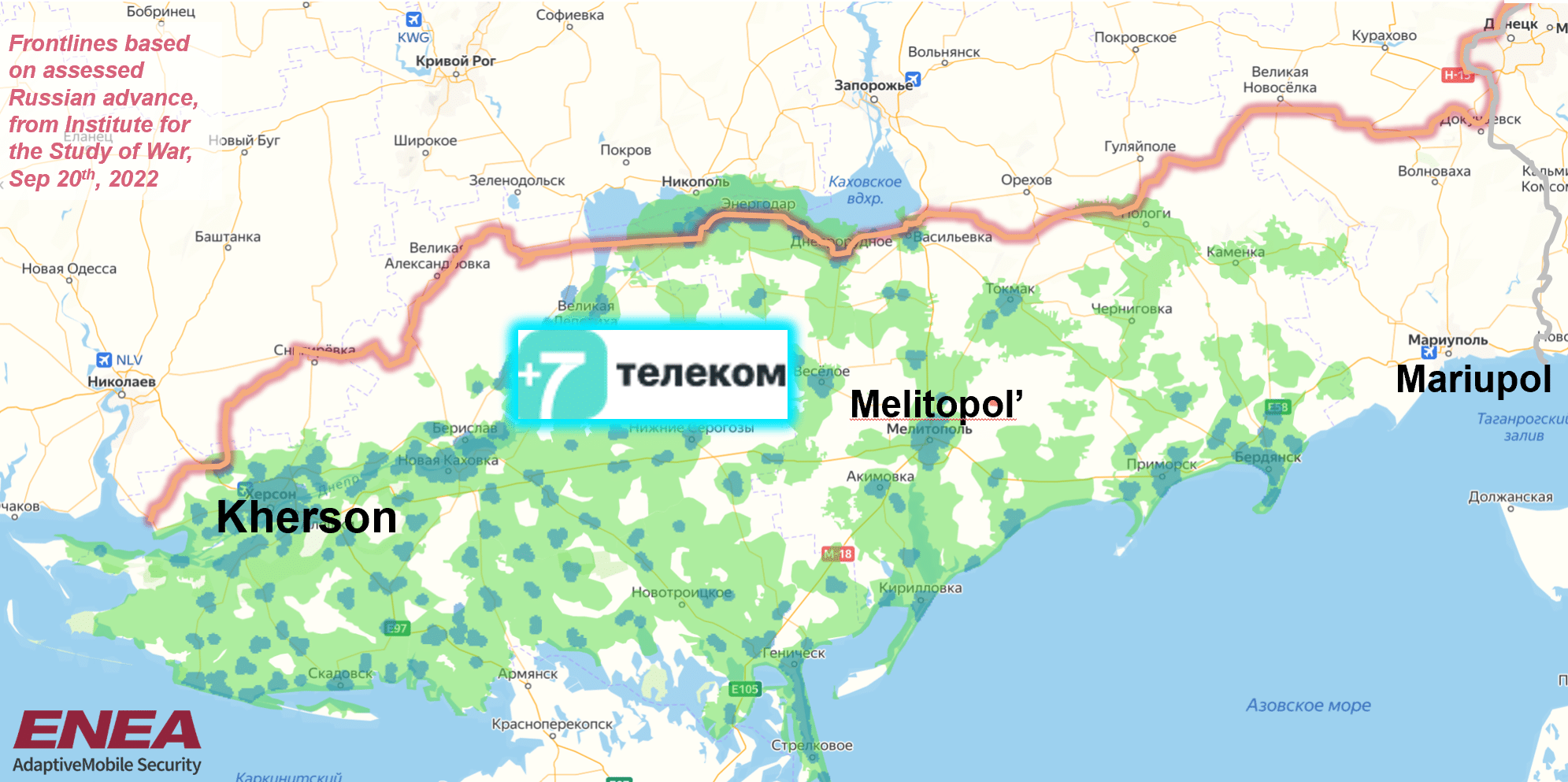
Network Coverage as reported by +7 Telecom. Frontlines as reported by ISW as of Sep 20th 2022
The choice of 2G and 4G (and no 3G) makes sense for a new mobile operator having the aim of first having a form of mobile communications over a wide area (2G), and then data connectivity in more urban areas (4G). Media reports have also strongly linked +7 Telecom with K-Telecom. K-Telecom is one of the 4 unrecognized Mobile Operators formed on the territory of Crimea and Sevastopol after its illegal annexation by Russia. Like the Donbas, and now southern Ukraine, the ‘main’ Russian mobile operators have tended not to expand into these areas, for fear of sanctions. This means that companies like K-Telecom (which trades under the name Win Mobile) have over time replaced the Ukrainian Mobile Operators in the area. A screenshot of the SIM Cards in the Russia-1 video used on the territory for +7 Telecom also shows the K-Telecom name being used, showing the connection.
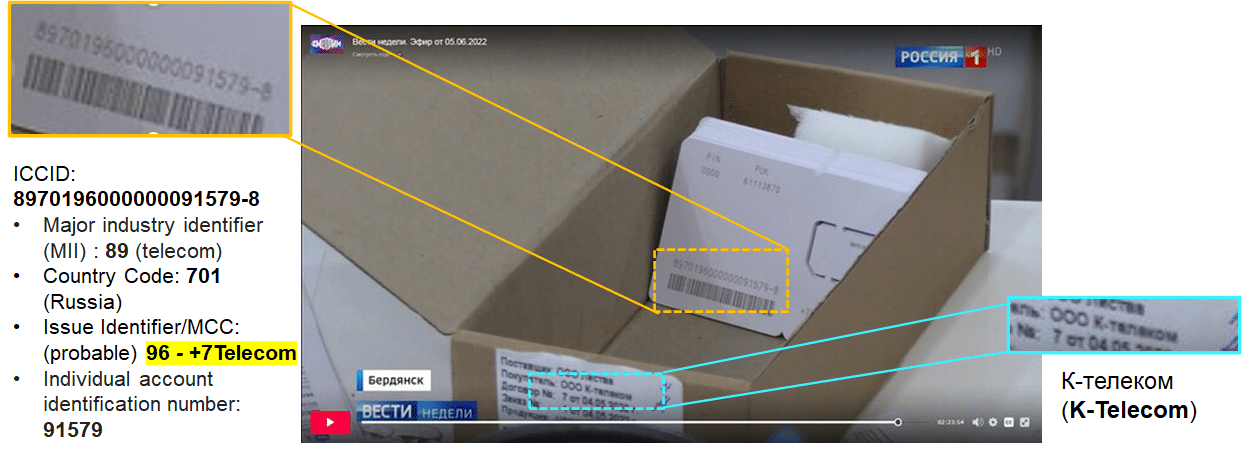
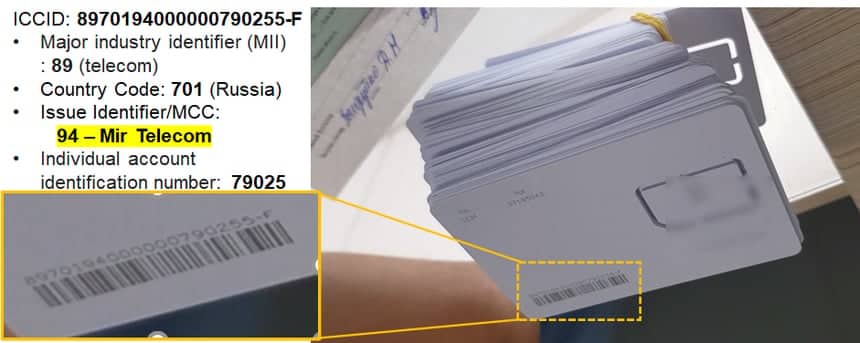
+7 Telecom SIM Card, as featured on Russia-1 , courtesy of cnews.ru
Notably this screenshot can also allow us to make some rough estimates of the number of SIM Cards available. The ICCID is roughly visible, and using that we can confirm the Mobile Country code (MCC), partially confirm the Mobile Network Code (MNC). Interestingly, we can also determine the number of SIM Cards printed (less than 100k at this stage). This differs from one report at the end of June where total subscribers for +7 Telecom around 200k, although there is nothing to stop additional SIM Cards being distributed if available.
MirTelecom
The final, and newest Mobile Operator the Russians have established is MirTelecom. Like +7 Telecom it uses a Russian unallocated area code – +7 990, – the same as +7 Telecom, and it uses a new Russian MCC MNC of 250-94. According to their coverage map this mobile operator is active in Kherson and Zaporizhzhia.
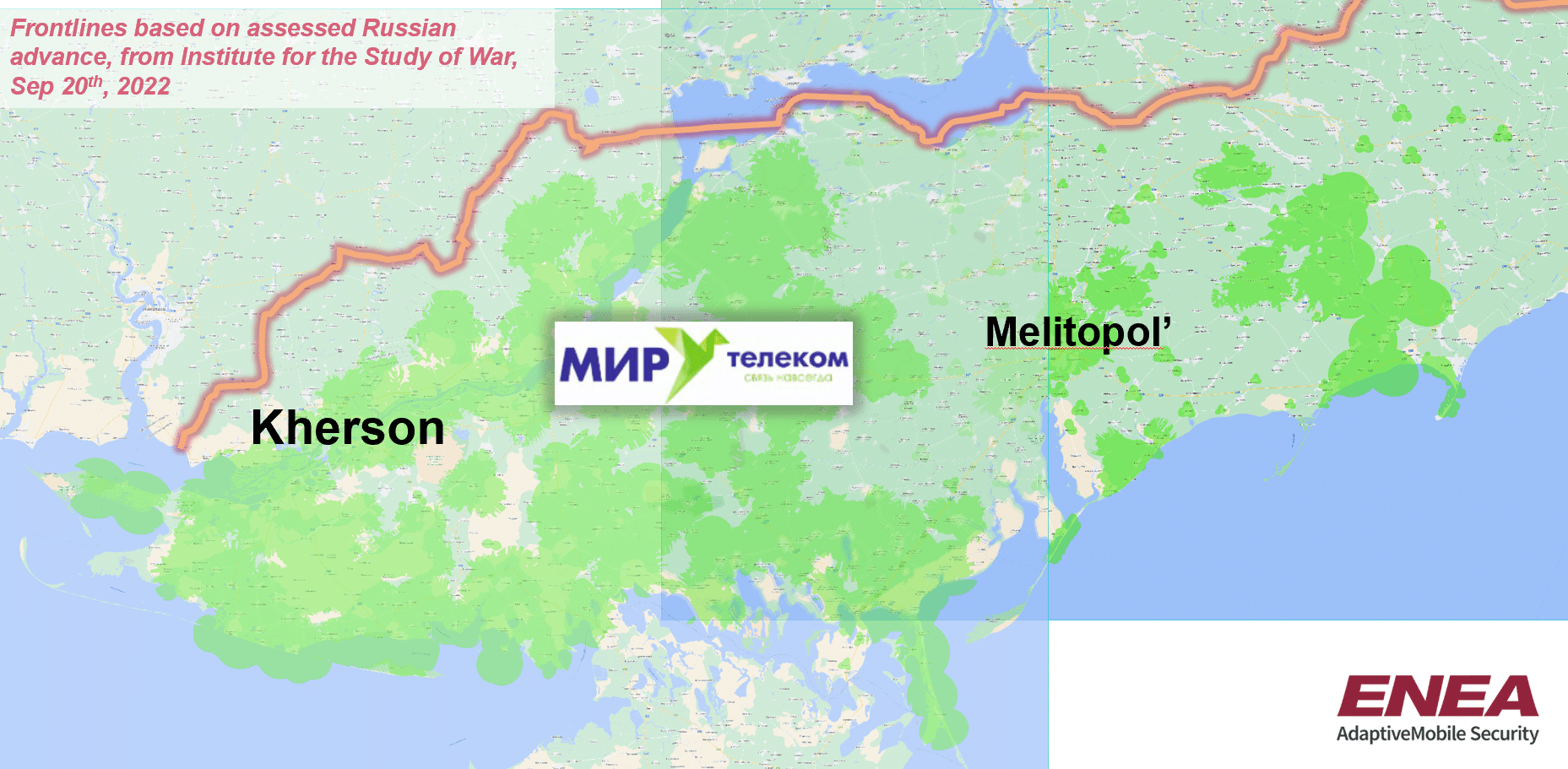
Network Coverage as reported by MirTelecom. Frontlines as reported by ISW as of Sep 20th 2022
An interesting point is that previously it was also active in part of the occupied Kharkiv region. This has been validated by reports from the area. However, with the recent Ukrainian successes in this area this material was hastily removed from their website, although a 2G coverage map is still available at the time of this blog. The coverage maps on the MirTelecom website only cover 2G, but there are also news reports from this operator that they also have 4G base stations active, which seems plausible. Like +7 Telecom there are screenshots of MirTelecom SIM Cards -taken from a video that is no longer available. This allows us to confirm the MCC-MNC, as well as to estimate the number of SIM Cards printed to date (again less than 100k).
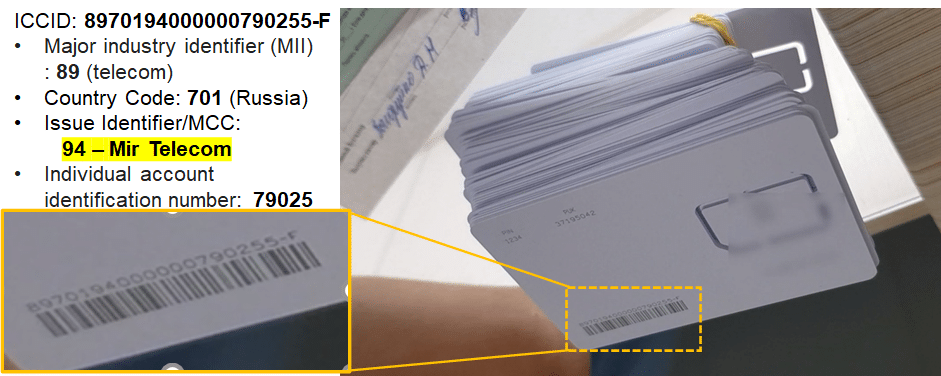
MirTelecom SIM Card – with MNC 94 used
Finding hidden associations via USSD
As part of our research, we attempted to see whether there were any connections between these new mobile operators (MirTelecom and +7 Telecom) and the existing Donbas and Crimea unlicensed Russian mobile operators. One way we did this is by looking at USSD – Unstructured Supplementary Service Data – codes advertised by the respective companies. These are codes which are programmed in the network equipment of mobile operators, and which tend not to be entirely common between different mobile operators in a country. Rather they reflect design choices and configurations of a mobile operator. Using these codes on your handset allows you to do various functions, example would include request someone to call you back, find out your own phone number, find your credit balance, transfer credit to someone else and so on. They have tended to be superseded in most other operators in the rest of Europe – you can use mobile apps for these kinds of functions – but in operators that have lower speed networks or places with connectivity issues they work well.
There is always an element of uncertainly in trying to compare these – we did not physically activate the codes with SIM cards from these operators. Instead we relied on what the mobile operators themselves report, and they describe in different ways what may or may not be the same thing. However, based on the wording, and more importantly the use of the codes themselves we could see some strong connections. A table showing the USSD codes of all 8 Russian separatist mobile operators in Ukraine is below:
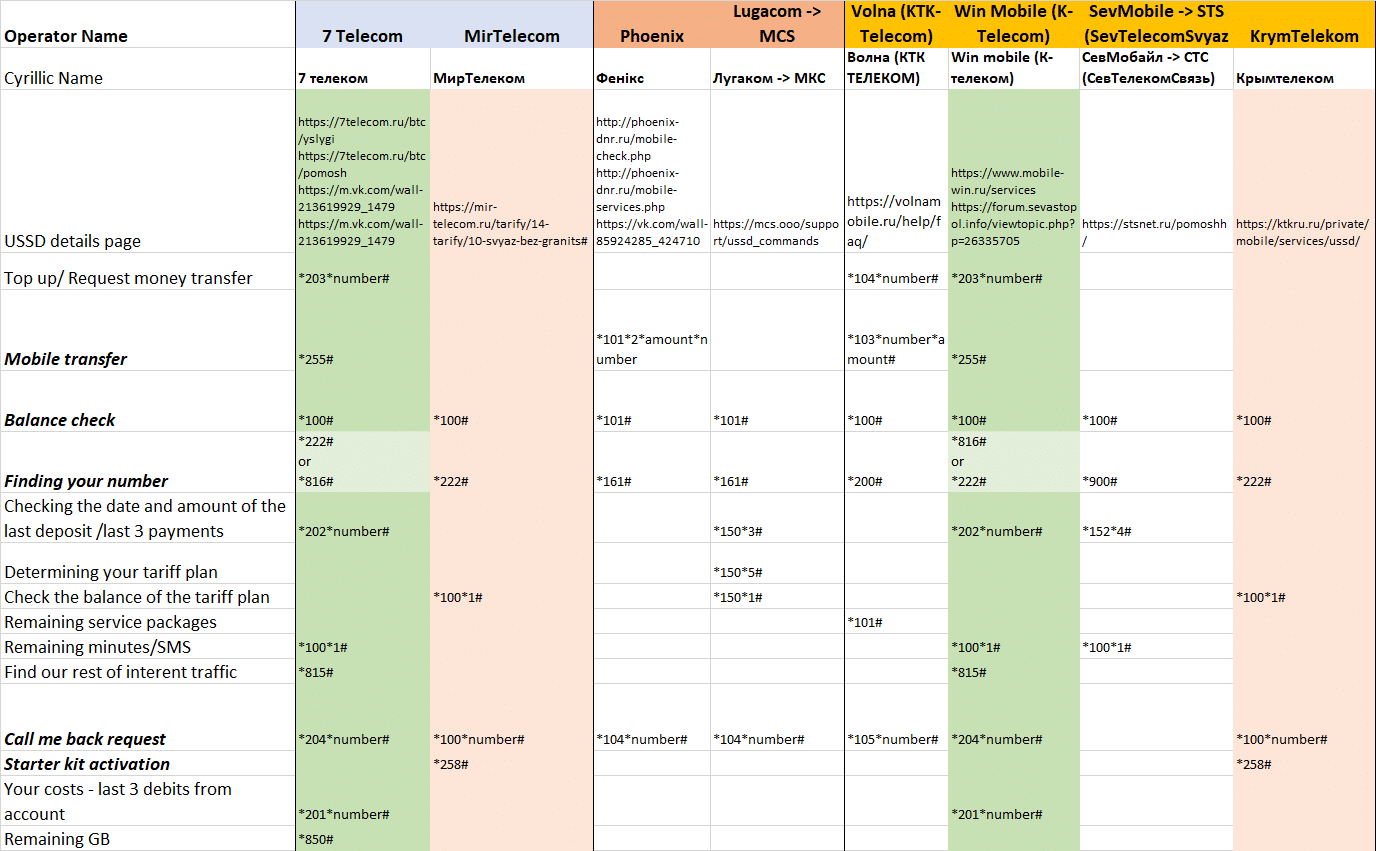
USSD Codes used by unlicensed Russian Operators in Southern Ukraine/Donbas/Crimea
Basing on the distribution and use of USSD codes between the new operators in the south and the Crimean opcos, we observed strong similarities between 7 Telecom and the Crimea operator K-Telecom (win mobile). This was already reported in the Russian media, but it helps strengthens the theory behind the method of using shared USSD codes. However our research show similarity between MirTelecom and the Crimean Operator KrymTelecom as well. This information is not in public knowledge, although we could see that it has been hinted at on social media.
This method of comparing mobile operators using USSD commands has not generally been done before. While it may be thought that it would be obvious that all mobile operators in a country share USSD codes this does not happen in practice. Our interpretation is that generally less complex commands might be common (like balance check), but the more complex the command (like credit transfer) or a request to be called back, the less similar the mobile operators are. While some codes are shared, like a balance check, you can see that MirTelecom and KrymTelecom have the exact same codes for “Starter kit activation”: (*258’#) and the “call me back” : (*100*number#) functions amongst others. This would not be expected to happen for two unassociated or unconnected mobile operators. As for why these USSD codes are common, and the exact nature of the connection between MirTelecom/KrymTelecom , we cannot say for certain. This could range anywhere from ownership to technical assistance to shared network configurations, or any combination of these. However, at the least it shows possible technical assistance technically to these new Mobile Operators from the existing unlicensed Russian mobile operators in Crimea.
Why so many Mobile Operators, so soon?
One other important point is the speed and sheer number of these new mobile operators. It took over 2 years for 4 unlicensed Russian mobile operators to eventually deploy in Crimea, and that in the Donbas each partially occupied region – Luhansk and Donetsk only formed one single mobile operator in Jun 2015 – over a year after hostilities started in March 2014.
However, since February 2022, as well as the existing Donbas mobile operators expanding rapidly to cover occupied territory, we have seen in occupied Southern Ukraine not one, but two new mobile Operators being created in a matter of months. All of this has occurred while under high-intensity wartime situations, unlike the previous ~8 years. We can safely say that if Russia authorities were content with mobile communications for the use of a civilian population, then it would have only gone at the same pace as from 2014 to 2022 that occurred in Crimea and the Donbas. However, given the accelerated speed, and the desire for choice (there is now a choice of 3 Russian mobile operators in Southern Ukraine), we can speculate that the Russia objective is not only to quickly gain all the advantages of having their own mobile networks in the area – for both military as well as civilian use – but also by building in redundancy. We can see further evidence of that, in a new report from MirTelecom where they said that for a period of time due to technical work their subscribers could use the +7 Telecom network . This essentially emulated the Ukrainian approach from a few weeks after the start of the war, when they enabled national (emergency) roaming.
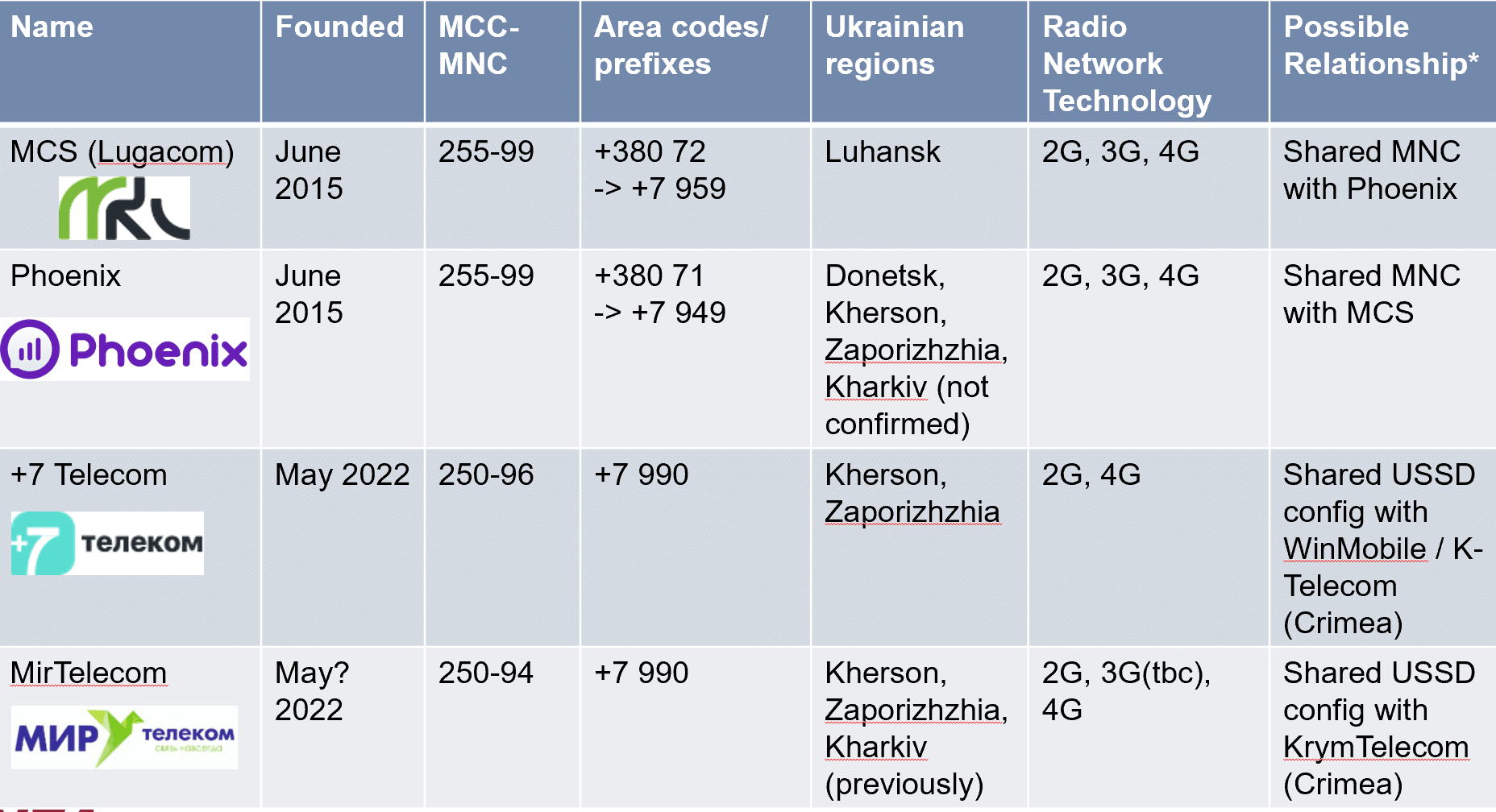
Overview table of unlicensed Russian Mobile Operators in occupied Southern Ukraine and the Donbas
Conclusion
Since the start of the 2022 Russian invasion of Ukraine, mobile networks, and the control of them has had a huge impact on the war. A lot of our focus at the start of the conflict involved making people aware of the innovative steps that the Ukrainian mobile operator community – mobile operators and regulator – did to both secure and maintain mobile connectivity in the country. This enabled Ukrainian society – military as well as civilian – to take advantage of this. We can see now in recent months that Russia has strongly focused on expanding existing and setting up new Russian-controlled mobile operators in captured areas to also gain an advantage. These new mobile operators have strong links to earlier Crimean Russian mobile operators, showing that existing commercial and logistic networks are being used to help deploy these. In addition, the greatly accelerated speed and the sheer number of Russian mobile operators, deployed in wartime conditions, show the high priority for Russia to roll out mobile connectivity in a warzone. This indicates the importance to Russia for telecom networks in these occupied areas, moving beyond a purely civilian ‘nice-to-have’ to a necessity. This is especially obvious given the well-known communication problems that Russian army forces have had, and the well documented use of mobile networks as a backup or even as a primary communication channel for the Russian military at times. Time will tell on the ultimate influence of these networks in the conflict.