There was great debate at the recent Capacity Media SMS World that AdaptiveMobile Security had the pleasure in attending, with CSO, Simeon Coney, partaking in a panel discussion on ‘How to increase Security in SMS’. With representatives from across the mobile ecosystem, the panel covered a breadth of topics and there was definitely more alignment than expected across the broad spectrum of speakers.
In this article we take a look back at what happened in the Capacity Media SMS WORLD 2021 panel on ‘Increasing Security in SMS’.
Increasing security in SMS Communications. Brief history
The session kicked off with a brief history of SMS Communications. The panellists highlighted the change in use case of SMS over the years. It’s amazing to think that SMS was originally intended as an application solution but grew legs and become popular as P2P (person-to-person) communications channel. Now, it’s interesting to see the full evolution of SMS and see its return to usage across A2P (application-to-person). However, unfortunately with the increase in enterprise usage we have seen exploitation of the SMS channel.
Origins of SS7
The origins of SS7 (Signalling System No. 7) was discussed, originating in 1975 and being an integral part of the signalling infrastructure that pulls everything together. SS7 enables Mobile Network Operators (MNOs) to pass calls and messages and various other information across to each other and also tells people where you are.
The SS7 was designed many years ago and the principle was it would just be operated by large formerly government owned organizations hence everything was assumed to be trusted. Nobody would have envisioned that it would become as large and expansive as it has been. Nor in fact even the nature of the volume of companies that are and the ability to steer you whilst roaming through different networks and check what network someone is on.
The expectation with SS7, was that everyone was going to be part of a nice closed, secure ecosystem and the reality is actually anyone that has any type of SS7 connection into the network has access to the whole world. That was really something that was quite unforeseen at the time and unfortunately it’s being quite heavily exploited.
Recent Phishing Attacks
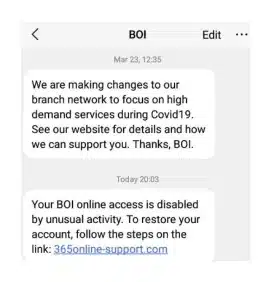
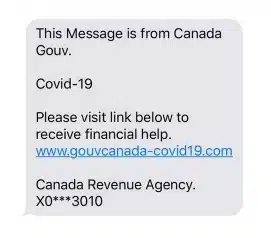
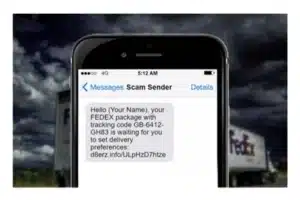
Then, the conversation turned towards the highly publicised recent UK Phishing attacks. The ecosystem has seen bad actors taking advantage of the Covid-19 landscape. The panel discussed some of the big threats in the past year.
Some of the spam we are seeing we have addressed in previous blog posts, social engineering scams such as banking fraud, Covid-19 related spam and many Package Delivery Spams. The consensus was that whole ecosystem needs to be involved in the solution, not just MNO, CPaas (Communications Platform as a Service), Government and regulators, all the stakeholders have to get together to tackle the security issues and collaborate to solve the issues.
How do we get the collaboration going to secure SMS?
There was an observations that possibly the biggest operator fraud concern is SIM farms as they are losing business because of it. Identity threat and phishing may not be a top issue for MNOs.
Yes, SMS phishing is a pain point for operators and they do want to stop spam to prevent losing their licences. However it is, enterprises such as financial institutions, healthcare, government, banks and ecommerce companies that worry most about identity theft and stealing of assets and the consequent fraud bills.
Also, the end user, the consumer, is losing key assets such as cryptocurrency wallets or personal health records. There was a suggestion that we need to focus more on the key constituents who feel the pain as well as the operators.
Are we doing enough to prevent pollution of the SMS Channel?
The MEF initiative have highlighted the issues to the mobile network operators and the aggregators. In some territories there is a 7726 reporting service, allowing consumers to raise awareness of bad SMS communications with networks.
Different territories are better at handling this than others, there needs to be a discussion on how to eliminate fraud and SPAM at a global level. Participating in industry trade bodies can help the ecosystem give a global centralised view but we need to do more as the global impact of SMS Spam is enormous.
What is the Global Impact of Securing SMS
Simeon Coney, CSO, explained in more detail the impact of the unsecure SMS. “So many people globally are affected by unsecure SMS, this is not something that is just in the domain or just the pain of the mobile network operators. It affects brands, enterprises and consumers worldwide.” He went on to explain that, when we look technically, there’s only a few places you can actually deliver protection from in the path of the message. Whether it be at the origination at the aggregator side, transit or in the delivery at the operator side.
The charging model as currently structured, charges per message, there’s no discrete identifiable value of security. People can’t easily pay a premium that guarantees end to end security, in reality the business case for security is on that is shared by everyone. So how do you reconcile the difference, where value is gained by a broad community, but the cost is borne by a subset. The panel added that if we keep the A2P SMS channel clean and secure then we promote the usage of the channel and we can increase the traffic running through it and thereby increase the value. So, in an ideal world the security will, in a way pay for itself. Read our post on SMS in a 5G World for more information.
Will we see a resurgence in Grey routes?
There was agreement that as companies put in protections there are cybercriminals thinking of new creative ways of avoiding the obstacles. It is a constant cat and mouse game and it is complicated. Even more so, as regulations are different across territories to minimise grey routes and bolster A2P grey route SMS messaging protection.
The ecosystem, need to think like hackers and with constant surveillance of traffic. If we lose trust and big brands stop using the channel for OTPs (one time passwords) via SMS then we lose the value of the business.
Sim Farms and GDPR
Sim farms originally existed in the Voice world but now they are impacting SMS. They can really hurt enterprises and now the potential fines with the implementation of GDPR are eye watering. Sim farms have multiple threat factors that grey routes don’t necessarily cover. MEF paper released a white paper on this recently.
If you use a Sim farm, that traffic may be in breach of GDPR, if you as an enterprise, send Personally Identifiable Information (PII) through a SIM farm that doesn’t manage data legally. The other issue is, do enterprises even know what does a SIM farm look like? Enterprises need to audit their suppliers.
A SIM farmer could be harvesting that data, eg they could know they you have recently done a motor tax return and try a phishing mail based on this information. With operators potentially suffering a double loss, losing to the grey route for the A2P sale and the P2P interconnect to rival operator to deliver that message.
How does an Enterprise choose a good messaging provider?
Getting the right people involved from the enterprise side from the outset is so important. Right now people are buying messaging based on price point and you’ve just got procurement in an organisation that quite possibly don’t care about the routes of traffic.
What enterprises really need to be doing is combining compliance and security people as well as understanding the business case for them. So once they understand the value of security then they can start to look at that audit feedback and can better justify actually not the cheapest route but the route that meets the needs of that business and that positive reinforcement will then start to trickle through the ecosystem.
Right now it’s such a convoluted web of delivery for organisations that are delivering to three four five hundred different countries. Using direct connections, or zero hops where possible, will help but there is a lack of understanding in enterprises how messages deliver end-to-end and the mobile ecosystem needs to help educate.
Is SMS the right channel for Two Factor Authentication (2FA)
The alternative channels haven’t been universally successful in taking over from 2FA yet. It was felt that enterprises want to continue using the SMS channel which has been effective for the delivery of 2FA but they want to be assured that messages are not hijacker, spoofed and the data is secure. The stakes for the enterprises are high with the potential fraud bills they could face.
Closing Remarks
There needs to be further education with MNOs and there needs to be at a minimum SMS Firewalls implemented. We would agree you need more than just an SMS Firewall but messaging intelligence is necessary to detect and respond to threats, protecting subscribers’ security and protecting brand reputation and revenues, including A2P SMS revenue.
Prescriptive regulation is not necessarily the best path to take as you are giving hackers guidelines to work around. You need to balance security with privacy to empower operators, enterprises and aggregators to deliver protection.
It’s not all doom and gloom, business messaging domain is growing. Looking at Juniper research there was c.3.5 trillion SMS Business messages in 2020 rising from 3.2 trillion in 2019, that’s a growth of 7% despite economic impact of COVID-19.