Koler Dropbox Ransomware APK Gets Its Worm On
Over the last 24 hours we have seen a new variant of the Android ransomware known as Koler become active in the United States.
Koler is a piece of malware that blackmails users of infected phones by blocking screen with an intimidating fake law enforcement notification page, and scares the victim to pay a “fine” to unlock their phone. This type of malware was first spotted in May this year blackmailing victims on Android devices. In July new reports suggested a new version that can also target PC’s.
This time though we have detected a new strategy to spread the infection. In this new variant of Koler (Worm.Koler) we found that it is now capable of self-replication via SMS messages which are sent to contacts in the address book of an infected device containing a bit.ly URL. This appears to be an attempt for the malware writer to improve the infection rate over earlier versions, which relied on hiding the malware in porn sites.
The attack starts with the victim receiving an SMS message from a phone number of someone they know that states:
someone made a profile named -Luca Pelliciari- and he uploaded some of your photos! is that you? [url=http://bit.ly/xxxxxx]http://bit.ly/xxxxxx[/url]
Interestingly the message has been used also in a Facebook scam in February this year spread through Facebook’s own messaging channel. Its possible that the malware author decided to use this text as they believed that it is good text content to ‘hook’ unsuspecting receivers of the message into clicking on the link.
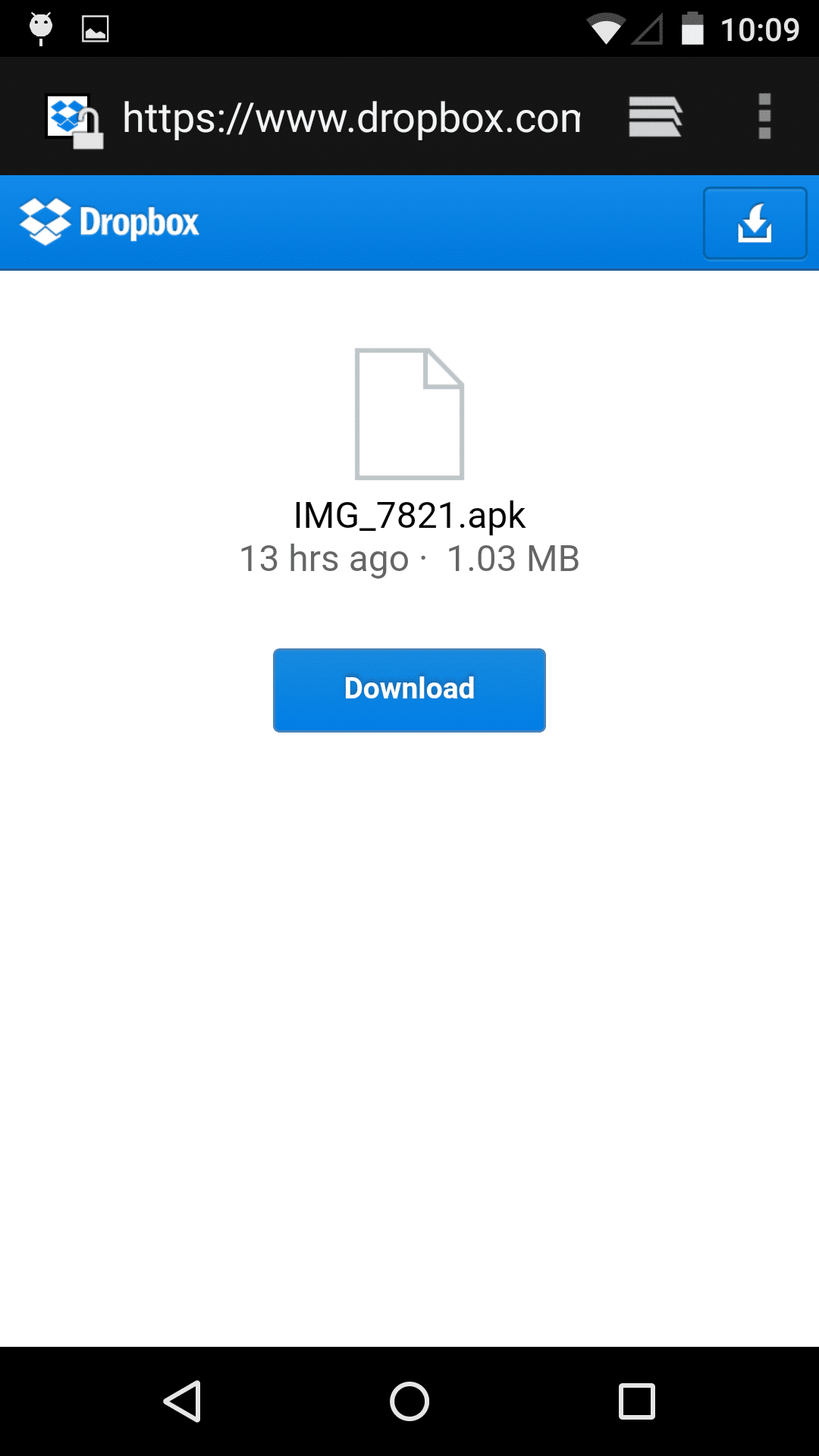
Hosting Page For Worm.Koler on DropBox
When a potential victim clicks on the link, the user is redirected to a DropBox page that offers user to download a ’PhotoViewer’ app. Once installed, it blocks user‘s screen with a fake FBI page, which states the device has been blocked for containing child pornography and zoophilia. The user then has the option to ‘wave the accusations’ and unlock the device by paying the “fine” using a Money Pak Voucher.

Worm.Koler as ‘PhotoViewer’
The device appears to be completely locked down with the screen on the phone blocked, so the user won’t be able to close the window, or deactivate the malware through the app manager. The victim is forced to buy a voucher as instructed on the blocking page, and send the voucher code to a malware author

Koler Ransomware App
It appears that the Worm.Koler malware writer(s) is trying to combine the techniques we have seen with SMS worms like Selfmite, with an Android ransomware attack . As we have seen in the recent Selfmite outbreaks, SMS worms rely on spreading the infection by spamming the victim’s contacts with text messages that contain download link to the .apk file. It’s also easier to trick a recipient to download and install malware via worm techniques, as it comes from someone known to the person.
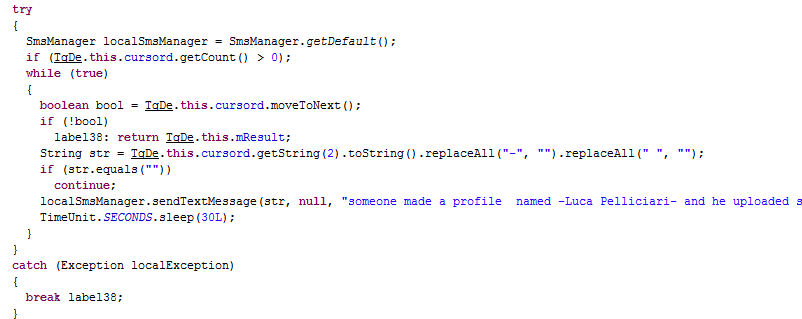
SMS sending routine
One interesting difference with this version of Koler and other SMS worm methods, is that Worm.Koler sends to all contacts only once, while in comparison Selfmite.B sends to all contacts in a loop.
Due to the Worm.Koler’s SMS distribution mechanism, we are seeing a rapid spread of infected devices since the 19th of October, which we believe to be the original outbreak date. During this short period, we have detected several hundred phones that exhibit signs of infection, across multiple US carriers. In addition to this, other mobile operators worldwide – predominantly in the Middle East, have been affected by this malware. We have already blocked several thousand worm messages being sent by infected devices on customer networks in North America network, as Worm.Kolar attempts to spread further via worm techniques.
As suggested by the statistics from bit.ly, the malware has got access to a large population, while the majority of click have been from the US, quite a few people have made contact to the malware apk through the bit.ly shorturl link around the world. As a result, we are expecting more infected devices appear in coming days.
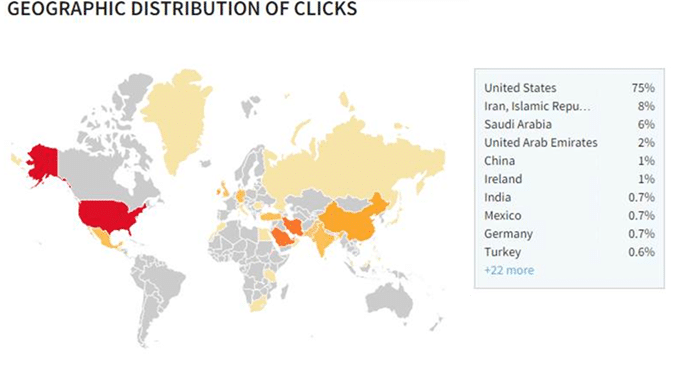
Source: bitly.com statistical service
To combat this threat, we have requested bit.ly to disable the link, and contacted dropbox to remove the malware file. We also actively blocking the message on our customer networks. In the interim however if you receive the message you should not click on it, and report it to your operator.
If you are unfortunately infected by the malware, you should never pay the ransom, as it won’t guarantee the unlocking of your device, and it will further encourage criminals to participate such ransom activity.
You can use following steps to remove the malware:
- Reboot phone into “Safe Mode”. Consult your phone manual for instructions on how to do this. Common device requirements are to hold volume up and volume down button simultaneously when restarting
- Remove the ‘PhotoViewer’ app using standard Android app uninstallation tool
IMG_7821.apk MD5: c7ee04bf3e42640ef6b5015b8af01f4f
Thanks to Denis Maslennikov and Cathal Mc Daid for contribution.





