5G RAN Security Protocol: Projections for the Future
In our recent blogs, we looked at the migration path from 4G to 5G and outlined the details in a white paper. This time, we look into the future of 5G security technology and make some projections.
This blog will extend the thoughts outlined in the report 5G – The Security of things to come, and takes an even deeper technical view.
5G networks security risks
5G Radio Access Networks (RAN) are widely now in operation or deployment phases. 5G core networks are also coming, and their deployments have been announced by many large mobile operators.
With 5G roaming on the horizon, now is a good time to reflect on the categories of risk we may face in the future for 5G interconnection traffic. We have seen that interconnection attackers in 2G, 3G or 4G networks have been interested in performing:
- Location Tracking
- Authentication Vector Theft
- SMS Theft e.g. banking TANs
- Traffic data theft e.g. for fraud
- Profile modification e.g. for fraud
- Eavesdropping
- Network data theft / Information extraction
- Ransomware (focus on the IT side of operators)
- DoS (for various reasons)
5G networks use a Service-Based Architecture (SBA). This is a “bus” architecture that connects all network functions in the core network with each other and allows communications between network functions e.g. to request information like user location.
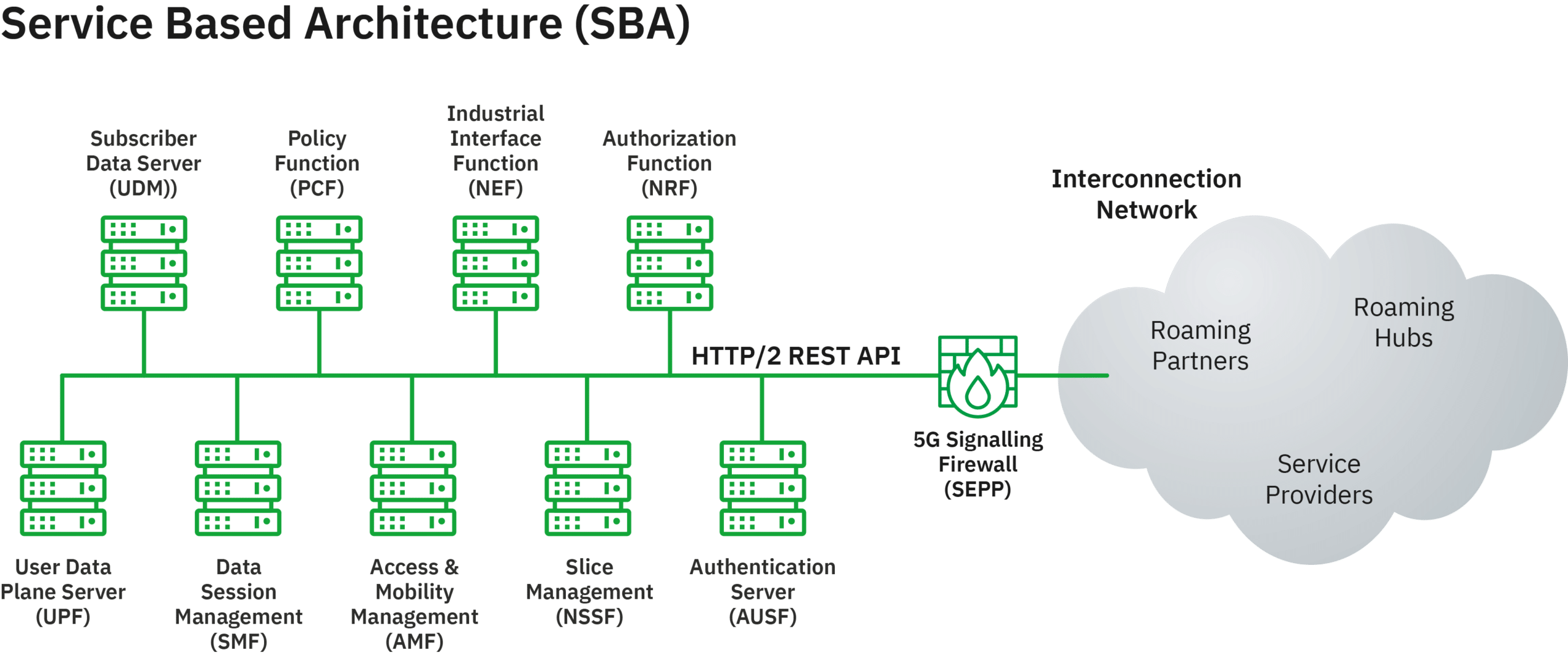
Figure 1: 5G Service Based Architecture (SBA)
This bus is also accessible from partner operators and protected from rogue nodes by the Security Edge Protection Proxy (SEPP). The service-based interfaces use REST API, HTTP/2 and JSON, which are all pretty common Internet protocols. Unfortunately, these protocols are also widely attacked. The wide adoption and usage of these protocols should not give us any false sense of security.
Nation-state cybersecurity and telecom surveillance is a very specialized service, which requires highly skilled tools, knowledge and people. Commercially, there are service companies that can be contracted for this kind of task. Nation-State intelligence agencies are also living in an outsourcing task business world.
Cyber-attack techniques evolve with technology
It is a fair guess that in the future those attackers will continue to have an interest in those aims above and will adapt their methods according to the target 5G networks and the available information and services.
Telecommunication technologies evolve, but many of the underlying principles and functionalities still remain the same e.g. for user mobility. Therefore, one can find commands in different generations, which perform a similar action and might be exploited by an attacker, retooling an old attack or adjacent attack method with not that much of an additional effort:
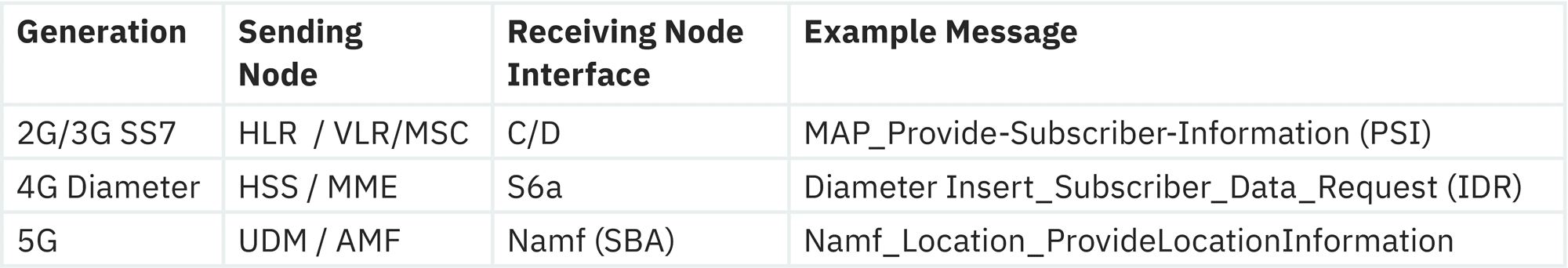
Table 1: Examples of potential location tracking attacks on unsecured networks through the generations
GSMA: security guidance for network operators
The GSMA, where most of the operators of the world are represented, has raised awareness on security issues and provides mobile network operators with guidance on how to improve their security.
The GSMA published for their members and also for non-members many specifications on how to improve the security of networks and all elements in it. Enea AdaptiveMobile Security contributes to many of those efforts through our global insight into real-life security threats that we see and analyze.
For example, the image below shows suspicious activities using diameter authentication and update location messages over the interconnection link:
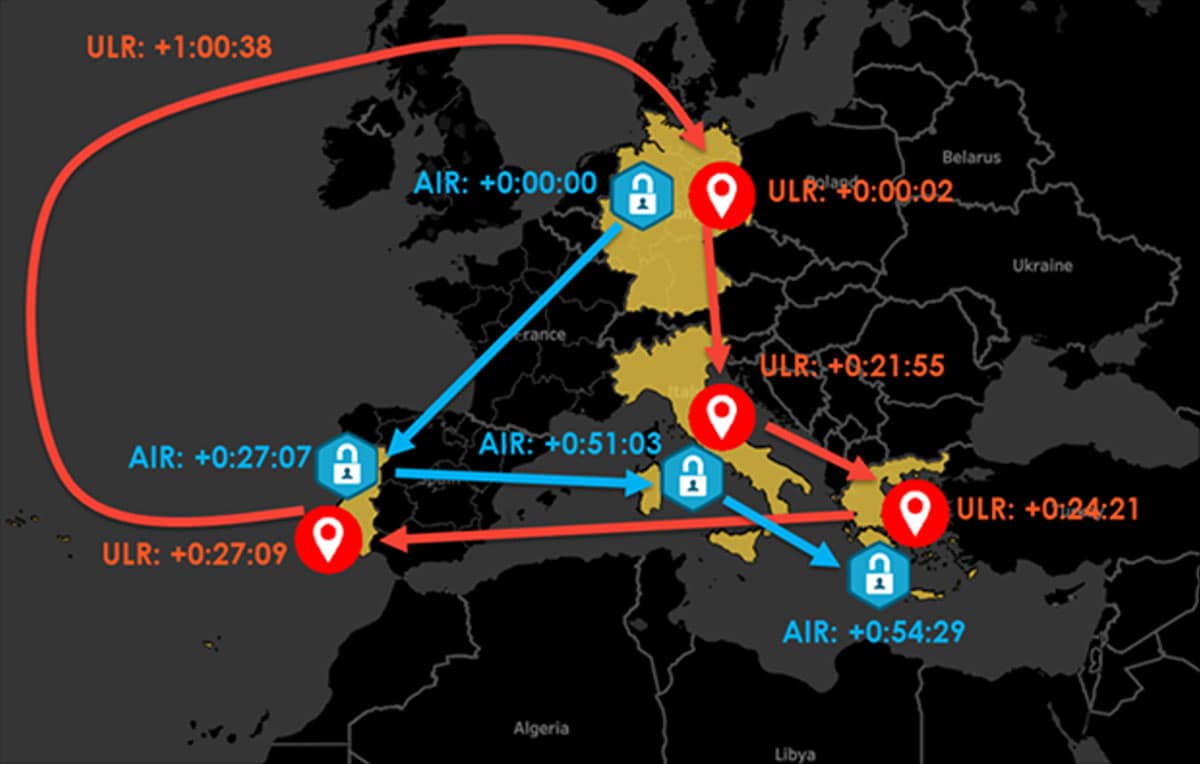
Figure 2: Suspicious activities using the diameter protocol
5G network attacks
In the telecommunication space, the number of core network node suppliers is quite limited, attackers can be assumed to have toolboxes for each of the individual suppliers and for each protocol.
In the recent past, attackers learned to vary and modify their attacks to disguise their traces and circumvent firewalls and filters. 5G core network architecture is much more IT’ish than the previous generations of core networks. Due to the availability of IT hacking tools for common protocols, speed of security and rule updates and awareness of vulnerabilities are of uttermost importance, as we can assume that attackers will modify existing IT tools to develop faster and more sophisticated 5G network attacks.
Why ransom an individual hospital when you can shut down a whole 5G enabled smart city or switch off the heating for a whole region when it’s -28 degrees Celsius? Therefore, we want to predict now what kind of technical threats we may face in future years…… let’s say 8 years….
Read now the second in a series of three 5G network security projections: Top 5G network security issues in 2028 >>
