Hacking Team & SS7 Protocol Hack: Can They Hear You Now?
By now, most people are aware that Hacking Team, an Italian-based seller of surveillance technology had their servers hacked and made public here. Wikileaks have taken the available emails and made them searchable.
This gives a unique opportunity for many of us in the security community to have an idea of what surveillance activities are undertaken, so we can better engineer defences against them. While the majority of Hacking Team work revolved around developing spyware for different types of fixed and mobile OS devices, i.e. on-device surveillance, they also seem to have come across a number of situations (and companies) which directly involved surveillance that occurs over the mobile operator’s networks themselves – the part of the mobile network that uses the SS7 protocol. We term this activity network surveillance. As we have previously revealed, showing the attacks that have occurred in Ukraine, security in the SS7 network has become of paramount importance for the mobile community, so knowing how these surveillance companies regard and use SS7 is essential. Based on the information that has become available, it seems that there is a wider group of commercial entities selling systems that allow surveillance over SS7 , and that these systems are for offer today.
Tracking the Team
First up, and somewhat most ironically, it seems that Hacking Team themselves took offence to two of their employees being tracked when these details showed up in 2 earlier Wikileaks documents:
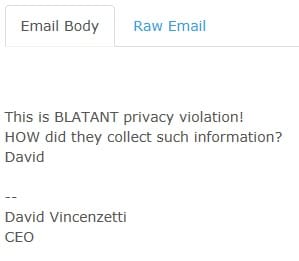
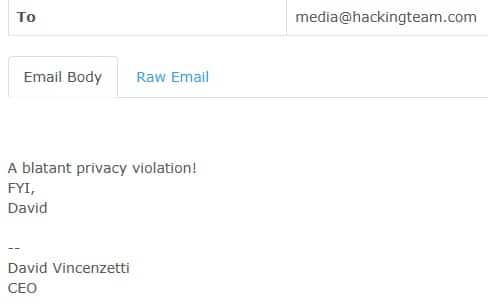
Their internal discussion talks about this tracking being done by a script that was set to run on SS7, as it seemed based on telephone number. They also theorise that this could only have been done via an insider contact in Telecom Italia (TIM). The reality though is given the imprecise nature of the lookups (being country only, not Cell-ID), then it is highly doubtful that an insider contact was needed in TIM. Instead, the information lookup could have been done using any one of a number of commercial SRI-SM* lookup companies which were available at the time. The ease of this, and the fact that a surveillance company like Hacking Team were not aware of this beforehand and could do little to protect themselves shows the impact that even simple methods using this network could allow.
Where the Clever Money is at
Another interesting point is that Hacking Team were approached by a representative from a company called CleverSig, looking for funding. While at the time CleverSig explain they are a small start-up, they do say they built and tested their own SS7 geolocation system. Here CleverSig specify that it costs US14k to 16k a month to have access to the SS7 network via an operator’s SS7 hub. While this seems sizable, a different way to look at this is that this is just over $22 an hour to have access to a network with connections to 600+ operators, as well as that SS7 connections are seemingly available if required:
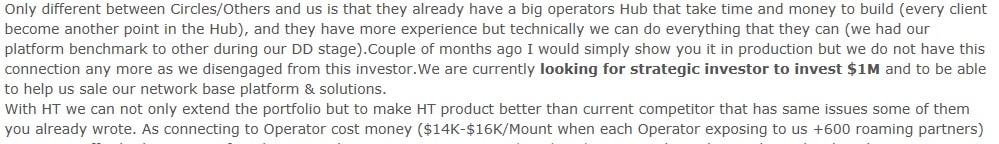
It seems that ultimately Hacking Team passed on this investment opportunity for various reasons, (too expensive and did not want ’secret’ agreement with mobile operators) and decided to ignore them. But the information does not stop there, CleverSig gives some interesting details in that they compare themselves to a different network surveillance company based in Bulgaria called Circles – a company with very little in the way of media exposure – but who we believe is this company , and which confirms that CleverSig are not an isolated case. Hacking Team seem also to have received specific information on other companies in the network surveillance world. As well as the aforementioned Circles & CleverSig , via a connection in Mexico HackingTeam were also referred to a brochure on a Geolocation system supplied from an Israeli company that their customer used, called GeoMatrix.
What is the Matrix?

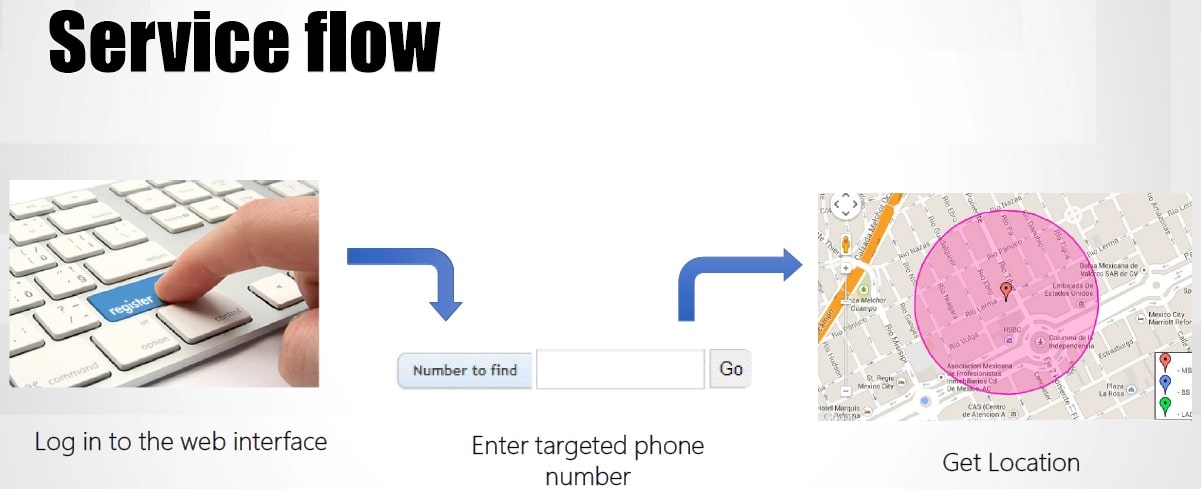
As well as the standard geolocation abilities, this brochure outlines some very interesting additional capabilities:
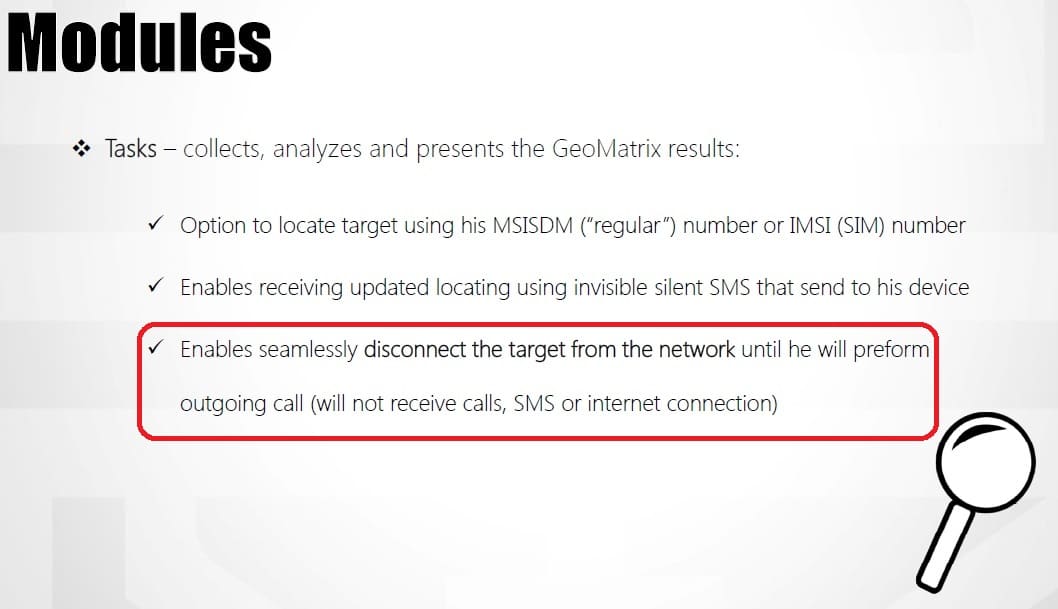
Ability to disconnect mobile phones from network
The last statement (which we have highlighted) shows a capability that has been known theoretically, but has not been seen advertised before for these systems. That is – as well as actually tracking a subscriber, they can also take control of a subscriber’s device, and prevent him from receiving call, text messages or using the internet. In effect the surveillance system is going beyond tracking to control, and the control in this case is extensive. As well as preventing them from receiving calls or text messages, another way to think about it is that it would basically make any messaging or voice app (encrypted or otherwise) unusable, and eventually force the person to make an outgoing ordinary call if they need to communicate with somebody. While the company of the provider of this solution is not stated explicitly in the mail, the solution itself resembles known systems advertised publicly.
Ultimately, while Hacking Team were primarily concerned with on-device surveillance, they have had exposure to network surveillance techniques and companies. This shows that the mis-use of SS7 technology for these methods is established and being sold on the market today by a variety of active participants.While Hacking Team may represent may be one of our best views on what on-device surveillance companies do today, this is only part of the whole picture, as their experiences clearly show there is a whole industry concerning in-network surveillance, that the security community should be aware of.
Many thanks to Ciaran Bradley for his contribution.
*SRI-SM = Send Routing Information for Short Message : a specific SS7 packet ’type’
