SMS Spammers Go Phishing in International Waters
Often when we receive a message on our handset, the eye is drawn to the sender, usually a long MSISDN in national format, but what about when you receive a message from an international source? Let’s assume for a moment you are a Colombian subscriber, and you receive a message from South Africa, Canada, or Pakistan for example. How likely are you to assume it is spam?
More subscribers than ever are receiving messages from international sources, including 2FA messages, Skype notifications and legitimate banking notifications. This opens a window for attackers to abuse SMS interconnection between countries to send out phishing messages and illegal content that is being blocked on specific networks in the country of destination.
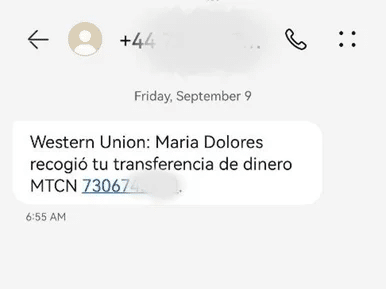
During the last year, we have observed this kind of activity.
Enea AdaptiveMobile Security’s Threat Intelligence Unit has been tackling the behavior. We have observed how spammers have been using a network in one particular country to execute a spam campaign targeting another country. In this particular case, we have identified SIM cards originating from a location outside of the United States attempting to introduce spam campaigns in the US.
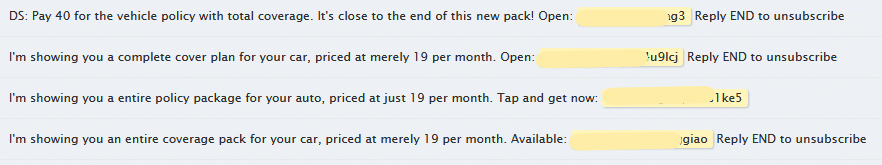
SMS interconnection abuse – anatomy of the spam message
Nowadays, scammers understand that a promising potential victim is an individual who is searching for ways to save money. Areas where people are particularly sensitive to value include:
-
- Gas prices
- Electricity bills
- Concert tickets
- Car insurance policies
In this case we are dealing with messages relating to car insurance. Spammers are offering full car insurance for a minimal monthly price. All the receiver has to do is click a URL.
The spammer’s intentions
As mentioned above, these attackers know their target’s weak spot, and have constructed a special, “too good to miss” offer to hook the victim. Once the user has opened the URL in the message and engages with the website, the risk of information theft is imminent. This could mean the user’s Social Security Number, or their credit/debit card PIN, for example. It’s a textbook case of SMS phishing.
How spammers work
One might envision these spammers as unstructured gangs, sending out blanket messages in the hopes of reaching the right targets and getting them to engage. The reality is that these are highly motivated and organized entities. They make their living based on revenues from these activities. They have techniques, procedures and even schedules to “work”.
In the case of these messages, we have identified groups of spammers who have been using a network in an alternative destination to target subscribers, avoiding detection on a particular operator’s network in the US which has spam protection in place.
The operators we have observed as being a source of this kind of malicious traffic are selected by spammers due to the low cost of interconnection messages, and because SIM cards are easy to get. Enea AdaptiveMobile Security’s Threat Intelligence Unit (TIU) has been successfully detecting and blocking this type of message and its mutations through a combination of techniques.
How do we stop spammers
With the advantage of our worldwide presence, we have the database and Intelligence necessary to stop spam campaigns and quickly identify any mutations, applying discovery and blocking techniques. This is one of the major benefits that our clients get from our threat intelligence services.
Discover more about our Threat Intelligence Unit https://www.enea.com/solutions/messaging-security/messaging-intelligence/