Singapore SMS Malware Worm Goes International
Android SMS Worm
Over the last 24 hours we have detected a new version of the SMS Worm for Android that was detected and warned above by Singapore’s Computer Emergency Response Team (SingCERT). Once it was reported by SingCERT the original worm (which has many different names including Dowgin, Nxuul & SmsLink), was profiled by AV companies as functioning as a worm that spread a lot like the Koler.Worm Ransomware. However the new version we have found seems considerably more advanced and sophisticated.
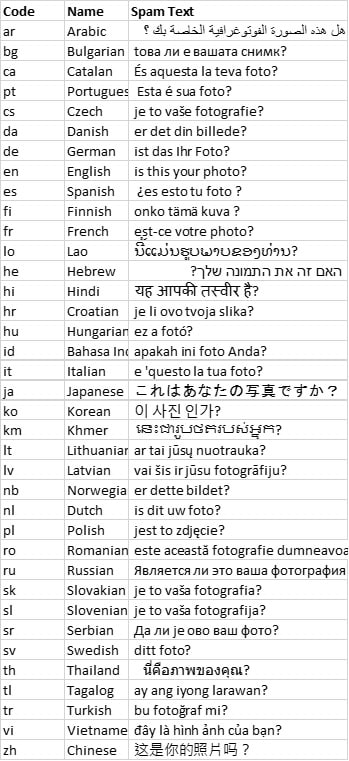
It uses the same worm mechanism, but has been designed to spread in multiple languages – not just in English like the original version, but in 37 different languages – depending on the host device. In addition the new version seems to have several new security features that have been implemented. Overall, this new version of this worm seems designed to be able to take the malware infection to different parts of the world, as well as being designed to be harder to analyse by mobile security companies.
The infection begins when the subscriber receives a text message, in the original version it was this:
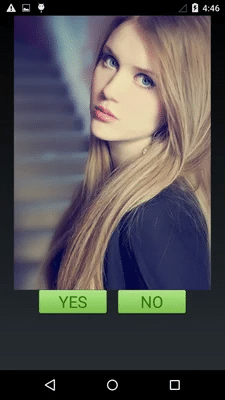
<Name> Is this your photo?
<Shortened link>
Where <Name> was selected from the contact list of the infected phone that send the text message. In the new version, the text can be the equivalent phrase in any one of 37 languages. If the user clicks the link, they have an option to install the application.
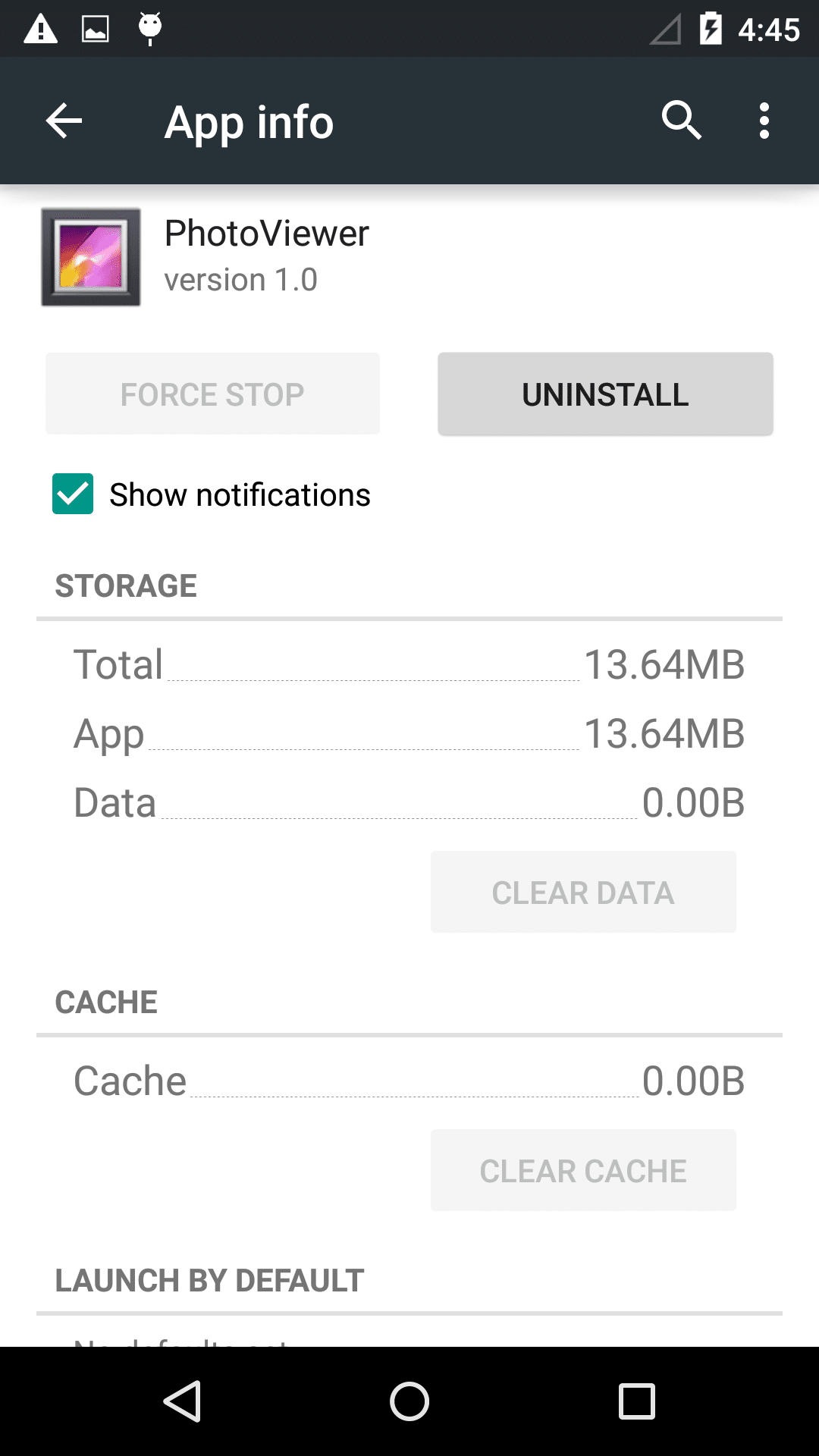
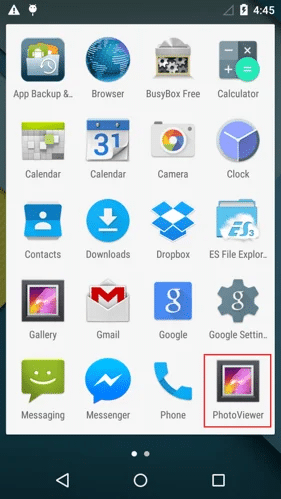
Once the application is installed, it is displayed as a ’PhotoViewer’ App
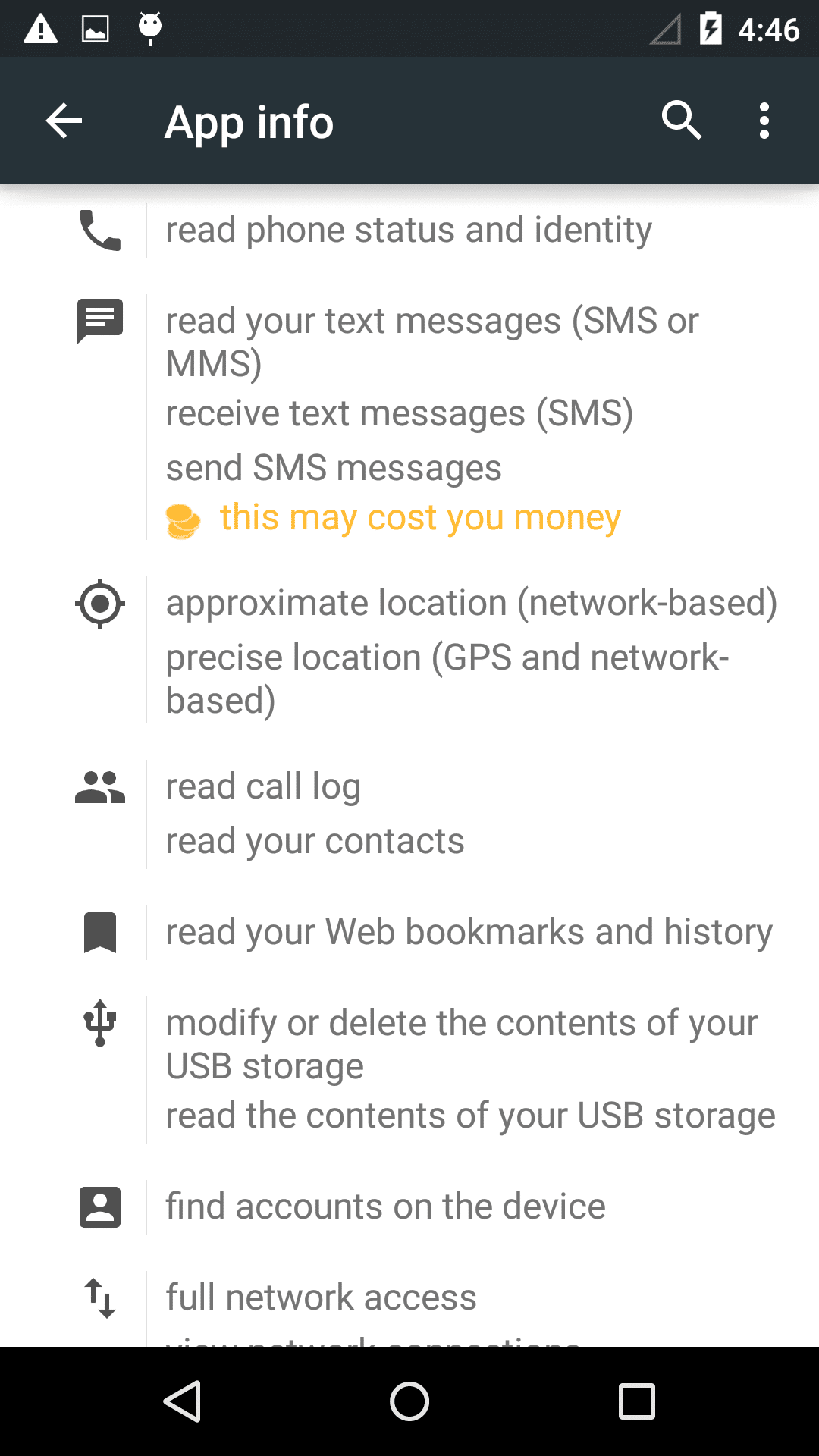
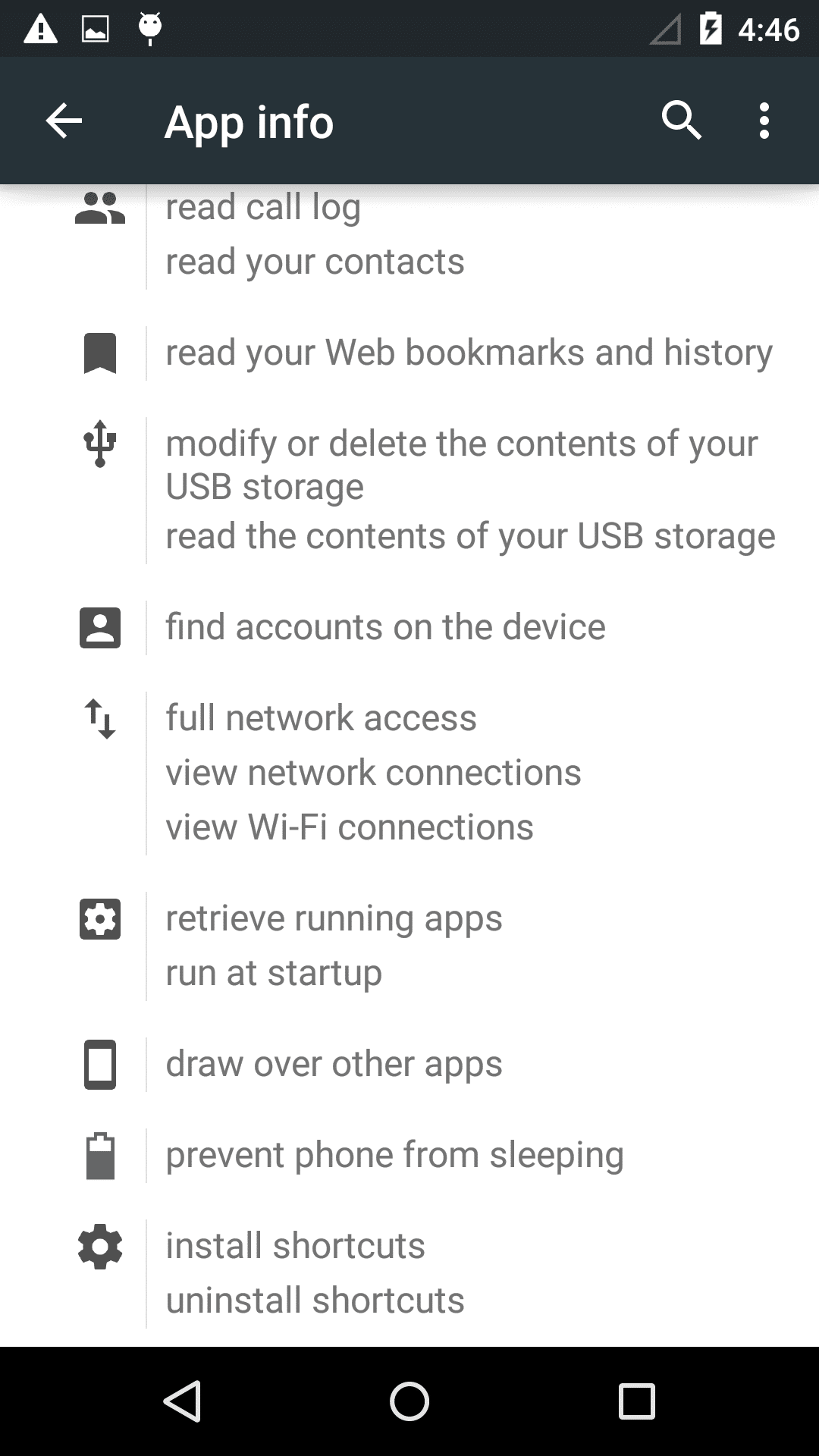
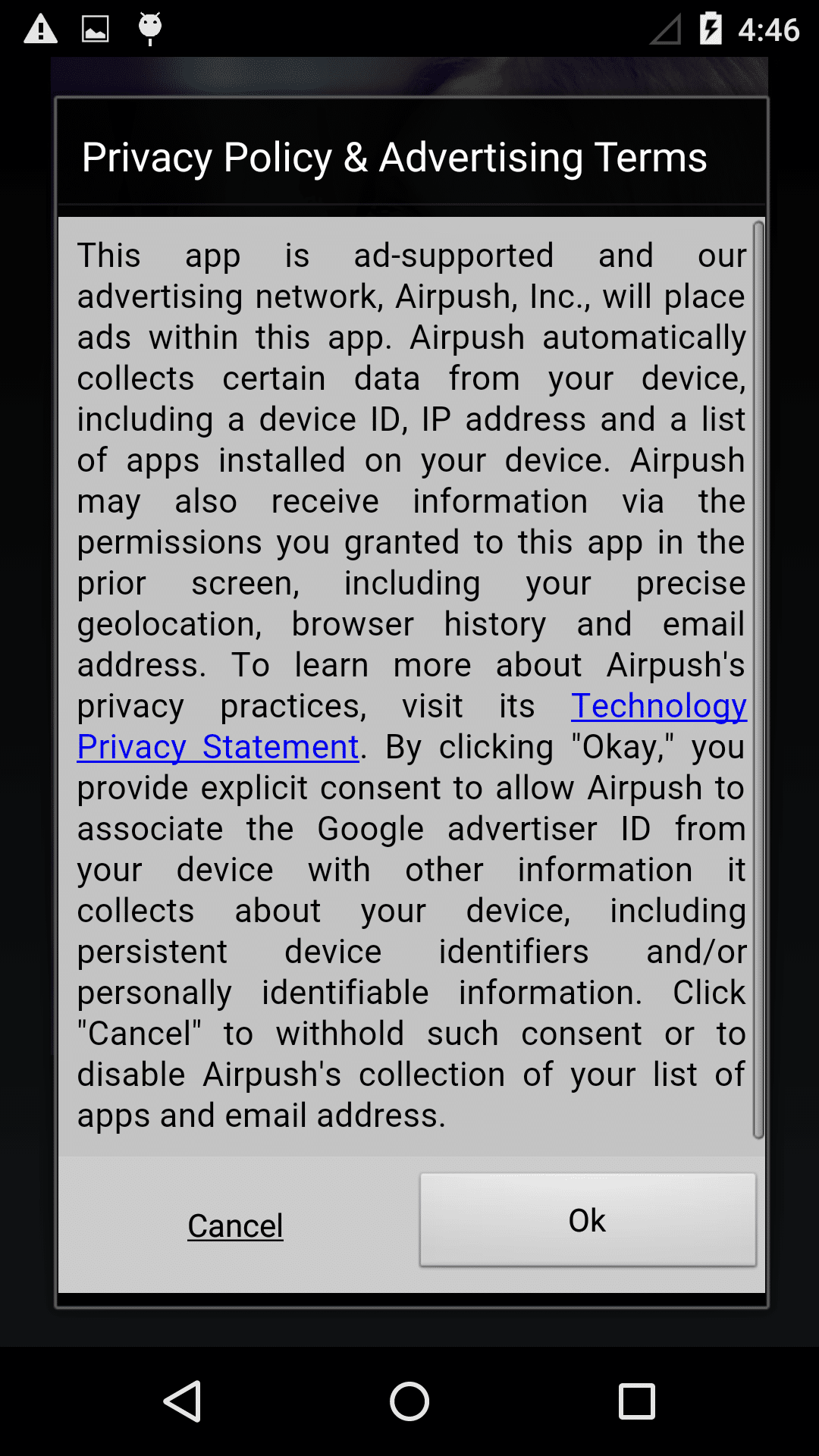
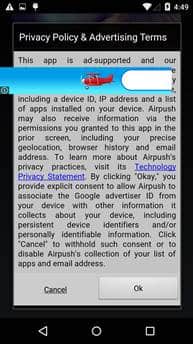
If the user clicks and opens the App, things get dangerous. When the malware starts it displays terms and conditions, If a user clicks ’ok’ it brings up a picture. The icon will hide from the screen afterwards.
Some important notes on what’s really happening:
- The ‘cancel’ button in the terms and conditions is actually unusable – the user cannot cancel
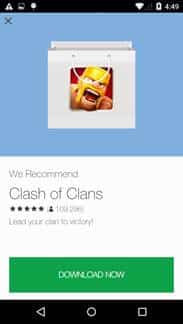
- The malware monetizes itself by displaying advertisements which the user cannot exit, and in effect make the phone unusable. How soon the phone gets locked up depends on the network connection. Once the app starts up, the advertising displays itself by adding a transparent layer to the screen. The various advertising libs embedded into the malware will start pulling advertising from the internet to overlay on the layer. This means the phone is essentially ’locked up’, as all clicks by the victim afterwards are on the adds or on the transparent layer and produce money for the malware authors. In fact the ads are so aggressive, they can start appearing even before the terms and conditions are accepted (as seen below).
Selection of Advertisements being displayed:

Background:
The Malware C&C is hardcoded to a set value in the malware, and from that the malware downloads various files, 2 files of note downloaded are:
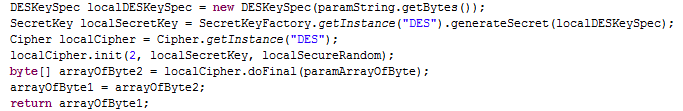
t.txt
We believe this file is a DES encrypted config, containing most likely the shortUrl link that is to be used in the text for downloading the apk, along with some other features.
json.txt
This contains ISO 639-1 language codes and the corresponding text. The languages selected are a mix of mainly European & East Asian languages – including English, Arabic, Spanish, German, Chinese, Japanese, Korean, Hindi, Russian, French – along with many others, see the bottom of this blog for the full list of languages and strings used.
The language used to populate the sms text worm string with is selected from the default language on the device:
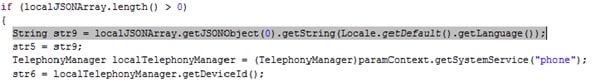
the use of the local language makes sense for an SMS worm basd mechanism, as recipients of the message would be less likely to click on the link (even from their friend), if it was not in a language in which they speak. We have previously seen that languages that spread through the local language make a better ’fit’ for sms spam, and this case is no exception
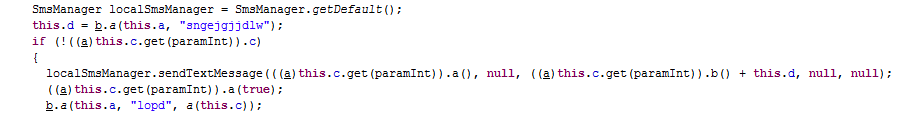
The malware then selectes people to send the spam message with the malware link via cycling through the user’s contacts list:
As well as having a vastly increased range of strings to use, and so many additional countries in which it could propagate, the new version of the malware contains many security enhancements, which seem have been introduced to provide additional protection from detection & analysis:
- More sophisticated obfuscation of the code
- Using encryption to protect information, including the Ad api accounts, as well as the short url shown previously:
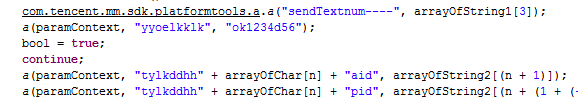
- The use of a WeChat micromessage (weixin) connection to report back information. This is a previously unseen development, and may herald the start of more usage of methods like this to try to hide communications/reporting.
The number of infected devices is currently still being determined, but as the malware outbreak is potentially only starting, it is not likely to be high in the early stages. To ensure this remains the case, mobile phone users in the affected areas should be wary of the below strings. What particular area is being targeted depends on the initial outbreak and the strings used. The earlier version was mostly reported in East Asia, especially in the Singapore area, and based on the languages used in this version to propagate with (including rarer ones such as Lao & Khmer), it seems likely as well this is also a main target.
On the other hand this version has been packaged with a full selection of languages from other parts of the world – including many European languages large and small – so it is not restricting itself. This local language selection seems one of the main innovations of this malware, and one we are likely to see again. Initial detections by us have so far been in the North American area, however we will continue to monitor for this infection worldwide
As always, to protect yourself you should:
- do not click on a link if you do not trust the contents
- If you install the malware by mistake, You can use following steps to remove the malware:
- Reboot phone into “Safe Mode”. Consult your phone manual for instructions on how to do this. Common device requirements are to hold volume up and volume down button simultaneously when restarting
- Remove the ‘PhotoViewer’ app using standard Android app uninstallation tool
Thanks to Yicheng Zhou, who analysed the malware and produced the research on which this blog is based.
MD5 : 7d0d14e96f26350bd27d85634e826969
Languages/Strings: