How Can the Telecom Security Industry Improve Telco Security?
Summary
- The Telecom industry needs a specific language to share information about specific threat actors
- Having a MITRE ATT&CK framework for mobile networks will help share knowledge of what telecom attackers do and help the unification of IT and telecom security mutual understanding
- Industry should support this and other new ways to share information
On Wednesday 20th October, AdaptiveMobile Security CTO, Cathal McDaid, took part in HardenStance’s annual Telecom Threat Intelligence Summit, with a presentation sharing his insights into lessons the telecom security ecosystem can learn from IT security. The following post shares highlights from his talk.
Need for a specific language to share information on specific threat actors in the telecom industry
The telecoms security ecosystem needs to share information better, and one of the ways we can do this is by learning lessons from those in the world of IT security. We need to think about adopting more effective ways of identifying threats and sharing information and intelligence about them in a timely manner.
This includes sharing information about threats including what exactly a threat is and whether you can recognise one when you see it, and how you can most efficiently and effectively share information about it?
If you are paralyzed by terror, it can be difficult to share information, but it is critical that you convey any information you have in a structured manner which is going to make sense to people who receive it, so that they are able to act upon it.
Effective information sharing on telecommunication threats
The telecom industry has been quite effective in sharing information on some threats. To take one specific example, four years ago in Germany there were several news reports explaining how the Signaling System 7 (SS7) (the mobile device control plane protocol for 2G/3G) had been exploited. When the attackers had gotten access to this protocol, they were able to exploit and empty some subscribers’ bank accounts.
They did this by intercepting text messages which had been used for two-factor authentication to access the bank accounts. Typically, the SS7 protocol would be exploited more for surveillance and nation-state level type attacks.
What is interesting is that information about this vulnerability had been shared within the GSM Association prior to news of the attack emerging. Some of the information that was shared was Global Title data. This detailed where these attacks originated, and we identified the source and we associated it with other attack sources.
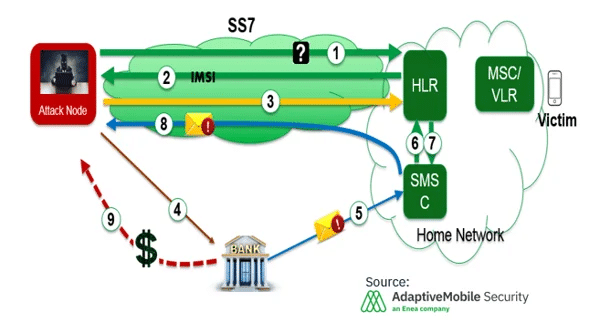
So, in advance of the attack, we had built up a map of this group, and we could see that they were using sources from UK, but also other countries such as Turkmenistan. When we saw this information, we communicated to the people being affected through multiple European operators including those who were not our customers because we understood that this information would be useful for them to try to deal with these attacks. We also shared this information with law enforcement.
Is sharing enough?
The case above is a good example which shows the benefits and capabilities of sharing, but what do you do for the larger types of attacks where you might not have all the information, and if you want to move beyond this specific type of threat?
In the SS7 case, we could share information because everybody understood that what we were sharing, and there was really no context that required interpretation.
But that technical level of sharing is not always possible, and in the telecoms ecosystem we have restrictions as to the amount of information we can share. Much of what we and our partners do is confidential, and we cannot share information about who has been targeted. There are privacy concerns to consider, and it is increasingly sensitive to talk about people’s identities.
At the same time, attackers are not technology fixed. If we were to build up a system that just shares information on SS7 or 3G, this is not going to work for 4G attacks executed via SMS, and it will not work for any type of combined attack. Attackers do not limit themselves to a particular technology or framework, they think about how they are going to carry out attacks and if they are going to be successful or not.
Improving telecommunication security by learning from IT security
We need a language to express the activity of threat actors. We need to have ways to share what it is they do and how they are doing it without necessarily focusing on the specifics of how they are going about it.
This “Fair sharing” would also allow for a greater understanding of the threats and collaborative efforts required to build defenses against them. If you can speak and conceptualize something, then you can better understand it – and then you can begin to see where your vulnerabilities may be and work to resolve them.
The question that comes down to is what type of information would you prefer?
Would you prefer a whole dump of information of somebody’s observations of something that happened? Or would you prefer factual, high-level, concise information which summarizes the tactics or techniques?
Most people would prefer to be given specific high-level information that means you are able to act on the threats which are present. Having all the details does not necessarily mean a better result for you – the defender – and this is what we want to do in the telecoms world.
Security companies can share information internally, but we need to build up a bigger, better way of working together. We know that these threat actors are not going to strike in any one specific place using one particular method. Attackers are going to do whatever they can to get the information they want. So, we need to think of the language and methods of how we share details of these attackers and the approaches they are using. Our response needs to be quick and efficient while still respecting privacy – and we need to develop a mindset of sharing as standard practice as opposed to it being something that happens occasionally.
MITRE ATT&CK framework for mobile network
Within the IT world, there is a common framework called the MITRE ATT&CK framework, which describes the detailed approach an attacker uses – in terms of tactics, techniques, and sub-techniques. It is widely supported, uses common tools, and is used throughout the IT industry, giving a common framework for people to speak about what attackers are doing at a high-level, and how a threat was discovered.
You may say that this is obviously what we should be doing in the telecoms world, unfortunately, we have some issues when it comes to using this kind of approach in protecting mobile networks.
There is a framework list of matrices for mobile, but this is very device-centric, covering Android and iOS, but it does not consider mobile networks. It does have a section which refers to network-based effects, but this is not separate and standalone and does not consider mobile network attack cases or anything to do with 5G.
There have been theoretical attempts in the past to create network-based models. These have had their issues as and the more you move away from MITRE, the more difficult it is to stay compatible with it.
Defining a MITRE ATT&CK model based on mobile core network attacks
While the industry agrees that there should be more information sharing, there is no easy way to do this or a clear way forward – especially in the areas of signaling or 5G as it arrives.
Our objective then is to define this framework and come up with a new way of threat information sharing and defining a model for all the adversary tactics and techniques that we see based on what we experience in real life.
It must consider a vast array of telecom protocols and any system we create must be future proofed. If 5G is going to take over the world, we need to ensure we have systems to share information and the threats to it, otherwise the world is in danger. It is already clear that 5G is not just a straight like-for-like replacement for 3G and 4G. Instead, it uses a whole different array of other protocols, but it is also built on top of 2G, 3G and 4G networks which will be around for years to come. So, it is a complex issue to solve.
Most importantly, any new framework must be compatible with the ATT&CK ecosystem and supported by the industry. There is no point in creating a theoretical system, it must have industry support, real-world application and be kept up to date.
AdaptiveMobile Security’s approach for extending MITRE ATT&CK for mobile network operators
We have proposed a method extending the MITRE ATT&CK ecosystem for mobile network operators which takes into account that there are many different types of telecom attacks, and also considers that these attacks are different from those in enterprise telecom networks. In particular, in telecom networks, the attackers are actually within the network, unlike in enterprises where they are coming from outside.
- Extend ATT&CK Mobile Matrix by mobile network aspects
What we propose is to extend the attack mobile matrix by adding a third matrix as well as iOS and Android, and then we would take parts from the existing matrix and use different types of subtexts to ensure that that we produce is compatible for everyone. This would mean we are able to reuse it, and other people from outside the telecom security industry would be able to look at this and understand and use it.
- Based on realistic attacks and adversary behaviour
This third, new matrix would be based on realistic attacks and adversary behaviors that we and other industry and mobile operators have seen in real life. Firstly, you take what is best from the mobile matrix and then you take one from the enterprise for IT and 5G, especially as some of the techniques are applicable for some of the specific attacks, we could see in 5G. And then we could take other ideas measures from the beta framework, but there will be a lot of new things we will have to add, and these will all be based on real attacks.
- Operator/industry input on important/notable attacks needed to create a widely accepted and used industry standard
As part of this, we have studied many of these attacks and mapped them out, and as the target audience for this we will need more operator and industry input on different types of attacks because there is little point for us to produce a standard for Enea AdaptiveMobile Security or for anybody else come up with a standard just for themselves. This is critical for all of us to share this type of information, because unless we do that, there is going to be a situation where we are constantly talking about different types of attacks, but we do not have a common language in which to share them.
This is a complicated piece of work, and it is not made any easier by the fact that the knowledge of attacks which is the core driver of building these techniques is in a much smaller group of people than the equivalent types of attacks in the IT world would be.
Our contribution for ATT&CK for mobile networks
We have been working on a table that visualises all the different techniques and tactics for sharing threat intelligence information. By capturing this data, we would be able to classify and categorize telecoms attacks. When this information is analysed, it could be used to build up ways to stop any such attacks and block them now and in the future.
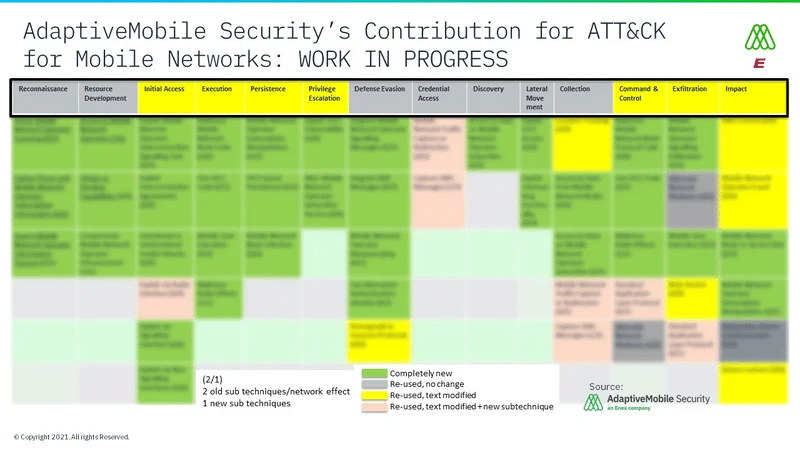
The proposed framework is in progress, led by Dr Silke Holtmanns, but we do need more involvement through industry partners and the GSMA.
In March this year, the European Union founded a Threat Intelligence Working Group and sharing within that group is also going to be important as they have recognised that telecoms are a critical part of national infrastructure, so we need to be able to communicate the threats that occur within our industry.
Creating this framework will not benefit any one specific security vendor, we are proposing a framework because we need this form of information sharing in our industry. We need a common language to communicate information about these threats and different types of attacks to better protect subscribers, networks and nations from attackers.

