Attack on the iPhones – Crashing iOS by SMS
iCloud account hacks on celebrities – such as Pippa Middleton – have been in the news again in the last few weeks. While these attacks often generate attention when they arise, and make people aware of personal information they are storing on iCloud, there is another, much larger ongoing campaign, using hacked iCloud Accounts over the last few months that iPhone users should be aware of. We reported on this problem of hacked iCloud accounts being used to send SMS a few weeks ago. Since that time there have been several changes, and the number of people being impacted by this has increased hugely.
To recap, the problem is due to attackers accessing people’s Apple iCloud accounts – probably through social engineering or by guessing the password to the account – and the iPhone that is paired to the iCloud account then being used to send large amount of iMessages spam to Chinese iPhone recipients. While iCloud hacks are nothing new, the real problem in this case revolves around the way that Apple have implemented the Send as SMS feature, specifically that this feature is used if the recipient iPhone is not reachable anymore using iMessage, and so SMSs are sent instead. This can have financial consequences for the person who owns the account, as well as the inconvenience of having their iCloud account hacked.
In a nutshell, iCloud accounts are being hacked, and the iPhone attached to the hacked account is then being used to send iMessage spam to Chinese iPhone recipients. But if the Chinese iPhone recipients are not connected to the data network, the iPhone attached to the hacked iCloud account will send the iMessage as a SMS instead, without any ability for the user to stop it.
How the Attacks happen
1. While the exact method in which the attacks get access to the iCloud accounts has not been proven, it is probable, that first the hackers obtain compromised iCloud account credentials using various known methods, such as phishing campaigns, guessing of passwords or some other means. The hacker then uses the stolen credentials and with them signs onto an Apple device of their own (Mac, iPod, iPhone, iPad, etc.). An example of a SMS phishing message for iCloud looks like the following:
2. Apple ID: An Unusual login attempt has been detected. Please Sign in and Continue. [url=http://www.apple.com.account.update.verification]http://www.apple.com.account.update.verification[/url].[REDACTED].com.br
3. These types of spams are very common, and have been reported on extensively in the past. This particular spam message points to this login screen:
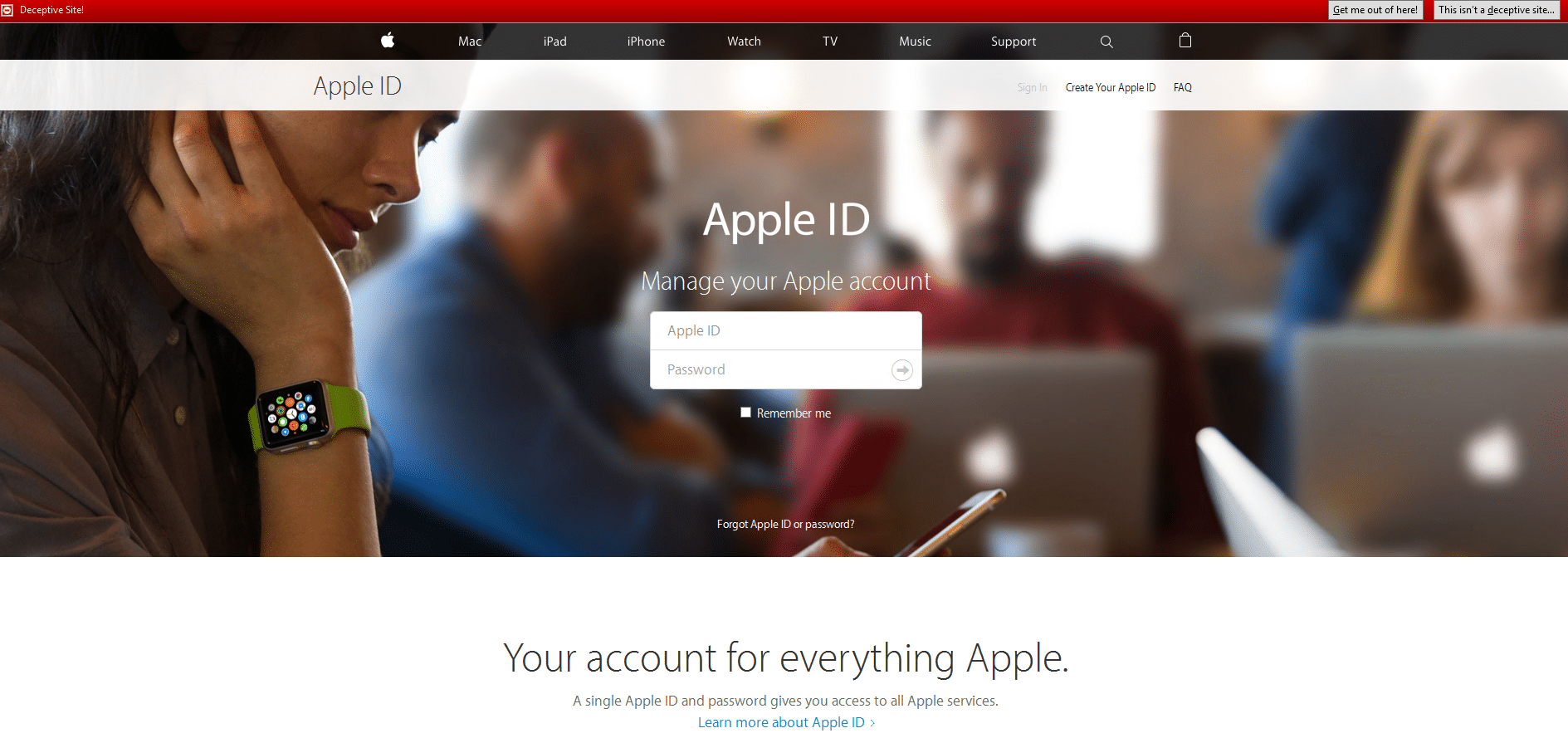
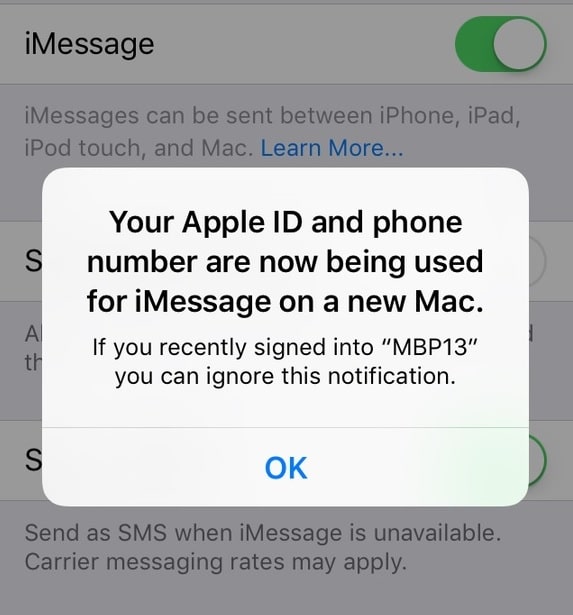
4. Once the hacker has the login details they will login and attach a new Apple device to the iCloud account. The user who owns the credentials will receive a brief notification on their iPhone that a new device has been paired, like the following; however the notification itself does not have an option to stop access
5. The hacker then sends spam messages to recipients in China using iMessage.
6. If the end recipient in China does not have a data connection at the time (i.e. has iMessage enabled on their iPhone but does not have a data connection through a 3G/4G or WiFi network), the original message is “downgraded” to SMS and sent to the end user. At this point, the message is sent via SMS from the associated user’s device to Chinese handsets.
This video shows exactly what is occurring for step 4, and how the sending message gets converted from iMessage to SMS:
Screenshot of a video showing the attack sequence on an iCloud account including mac and iPhone screens of attacker and user
The overall impact of this, as we covered, is as follows:
The iCloud account has been compromised and the associated iPhone to the account is being used to send iMessage/sms spam, prompting angry responses from those in China that receive the message.
Incidentially : this sometimes causes confusion to those whose account has been attacked, giving them the impression somehow that they are receiving the spam messages, as they did not sent the messages manually themselves
The user may end up paying to send potentially thousands of these SMS messages to China, causing a huge bill to them. This varies depending on the plan and the carrier the user has, but to give one example this may cost them $0.20 per SMS message sent. Some devices have been recorded sending thousands of messages so this bill could be sizable
The possibility that they may have their service disconnected by the mobile operator, for sending spam sms messages.
There is also the fact that the iCloud account that has been hacked/compromised in the first place, meaning the attackers may have access to any information in the account.
The Effect
In our initial blog, we reported that:
- We have seen over 3,200 phone numbers in North America had been affected in July & August, and these had sent over 280k spam sms messages, along with an unknown number of iMessage spam.
Since then, however there was a large escalation in sending activity. Cumulatively, (including July and August) by mid October we had detected over 11,500 phone numbers sending these messages, who had sent over 750k SMS messages. - To show this, the top graph below, is a moving average of total SMS spam activity from these iPhones detected within our customer operators in North America. You can see that the number of messages peaked in mid-September, and since then the overall volumes have declined. However, in the bottom graph, again using a moving average we can see that the number of active senders per day peaked later – at the end September/start October, and has actually remained higher than it was before the increase in mid-September.
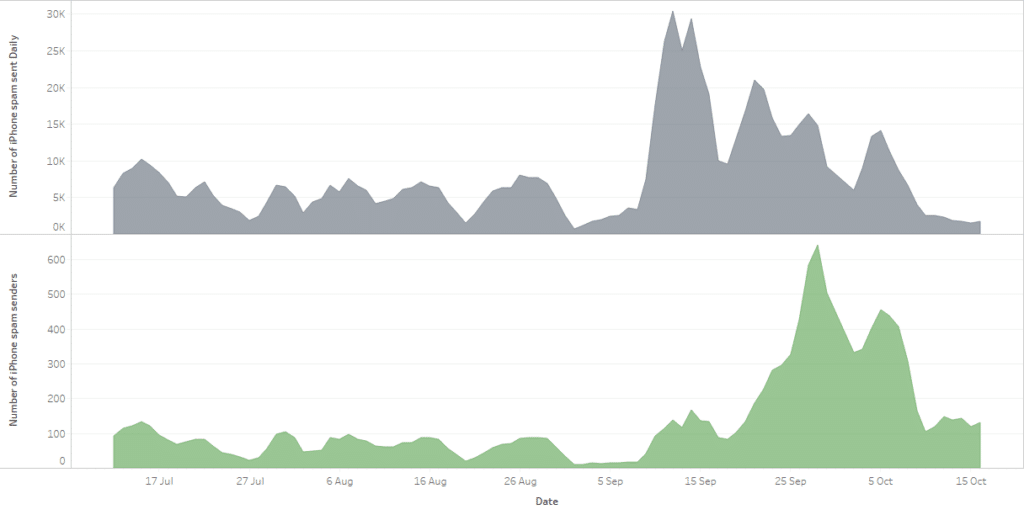
Graph showing the moving average of total iCloud hacking SMS spam activity on iPhones in North America
This is indicative that the spammers are now sending less spam messages per hacked account, presumably to improve effectiveness and avoid detection. It also shows that even though spam volumes and the number of spam-sending iPhones have declined from their peak, there is still an upward trend in compromised iCloud accounts and their associated iPhones. While numbers have declined since the spikes, the problem remains.
Indeed, even though the above stats is from North America you don’t have to look far to see evidence of people having their iCloud account hacked and iMessages being sent worldwide, with reports of people being affected in the UK and Singapore. iCloud accounts being hacked to send spam messages to China are a global phenomenon.
New Attacks
The other major change is in the type of messages being sent, whereas originally the type of scams being sent were mostly aggressive advertising campaigns, trying to sell counterfeit good, now we are seeing many more spam campaigns featured gambling websites. The content of these messages often are of the following format:
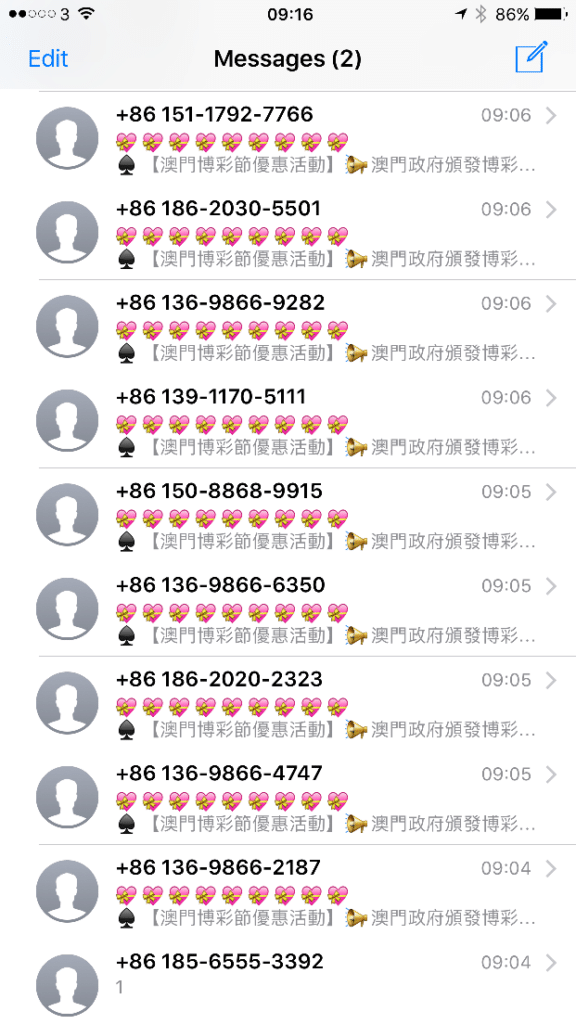
Log of Chinese SMS spam iPhone messages Chinese SMS spam iPhone message
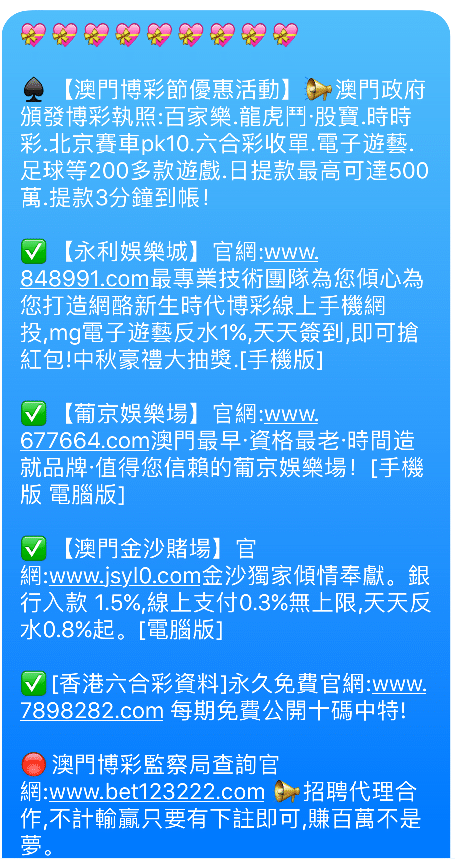
And their purpose is to direct the users to gambling websites, like the following:
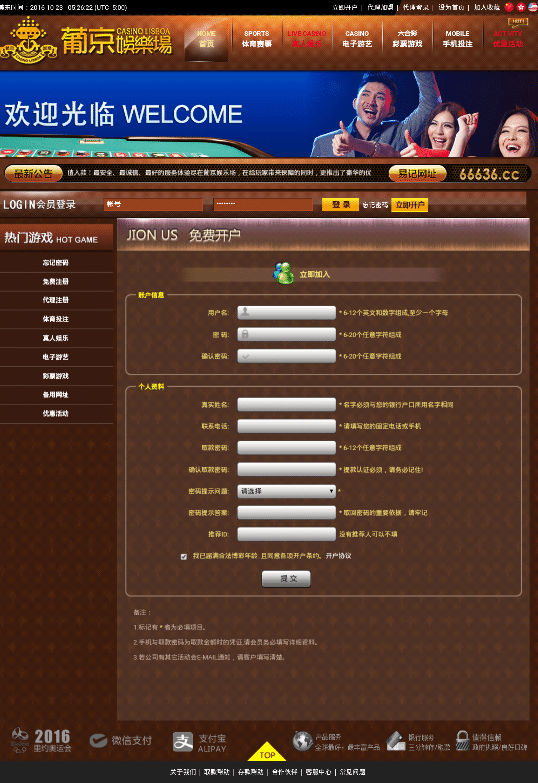
Landing page of Chinese spam website Chinese spam website
The fact that now there are now multiple different spam ‘campaigns’ is also worrying. This means that the criminals who gain access to the iCloud accounts, and send these messages may now be diversifying or offering their service to cover different types of spam. Whereas at the start it was fake goods, now it is being expanded to also include gambling advertisements. This is always a sign that attempts are being made to broaden the scope of what can be done with these hacked iCloud accounts.
Destination of the Attacks
The target for these attacks is still Chinese recipients, in fact it is quite interesting if we plot out the recipient number by the province in which they are registered. To give some background, in China, like North America, mobile numbers can be allocated by range to the province to which they are registered from. Using this method, we can plot out out the main geographic focus of attacks.
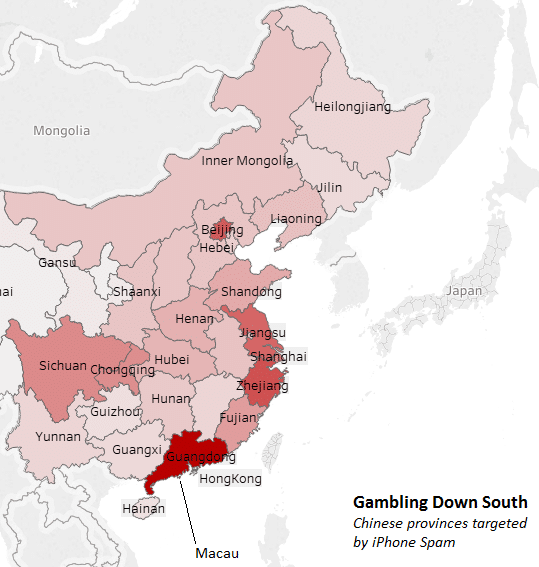
Map of China highlighting provinces targeted by gambling iPhone scam
Like the US, it is not the phone number’s actual location, but it is a good guide to see what areas are of primary focus. While it is generally spread out by region, we can see that the largest numbers of attacks are targeted to iPhones registered with phone numbers from Guangdong province in the south. This province is China’s most populous, but it is targeted much more than would be expected. One reason could be that Guangdong borders Macau and Hong Kong. This fits into the pattern for the recent change of iMessage spam to include advertising of gambling sites, as most, if not all of these are based in Macau. While gambling is officially illegal in China, Macau’s gambling industry is many times the size of Las Vegas, and so iPhone users from Guangdong may be disproportionally targeted as the spammers may want to focus on people from neighbouring areas.
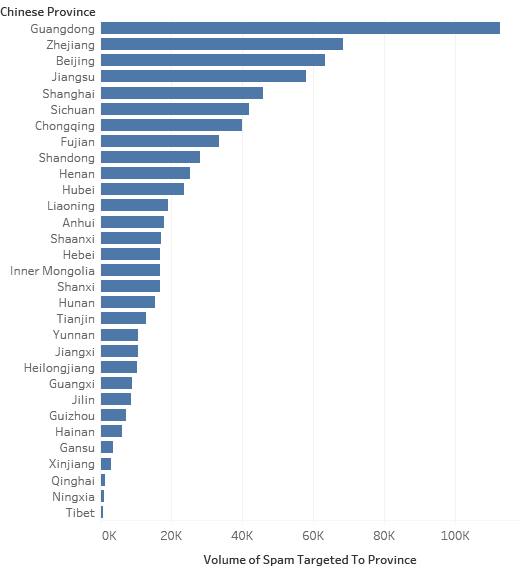
Vertical histogram displaying the volume of iPhone gambling spam targeted per Province
This geographic focus obviously means that the spam attacks are not random, and is another indication of the sophistication of the attacks. The purpose of the attacks in the first place is to send spam to Chinese iPhone subscribers, and so this ability to tailor the spam to certain regions means that the attackers can offer specific services for any spam they want to send in the future. We have covered before the out-sourcing of SMS spam sent to China to US devices, due to the attraction of sending spam from external sources, and the difficulty in sending spam within China, and these type of attacks are an extension of that.
How can mobile subscribers protect themselves?
We previous covered before some recommendations if you suspect that your iCloud account has been attacked, and you phone is sending these messages, so here they are again:
1) Go to https://appleid.apple.com, login using your iCloud account
2) Change your password
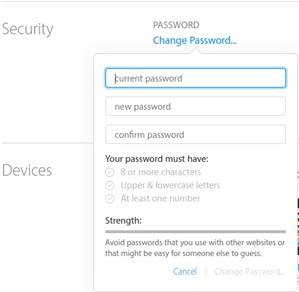
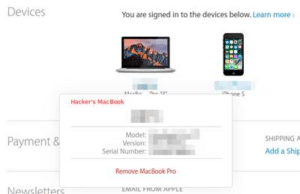
3) Unlink any devices that you don’t recognize
To this we can add to contact Apple if you are in any doubt (via social media or directly), – i.e. their twitter support handle is @AppleSupport, as they can explain and help you deal with the problem, and would be the primary source of information on what to do.
To prevent being hacked in the first place, there are also two other main recommendations
Its most likely that the attackers are getting access to the accounts by guessing the password or by using phishing techniques. So always use strong passwords, and always be careful if you get asked for your Apple login details in suspicious emails, text messages or websites.
Enable two step verification on your account. Details on how to do this are here, this means that future attempts to attach new devices will need to be verified by you. Note this procedure is different from two-factor authentication.
Finally, while mobile operators can detect and block these attacks when they switch to use SMS, there is actually little more they can do, as the source of the attack are from the iCloud accounts, attached to iPhones. Instead responsibility primarily lies with people to make sure they protect their account as much as possible, and with Apple to ensure that these attacks using the hacked iCloud accounts can’t happen. The first is easier said than done however, and in many cases the iCloud account access may have been obtained through a variety of methods, through social engineering, weak passwords or leaked account details. For the second, the best recommendation is to alert Apple when your iCloud account is hacked into, to make sure that they take action on their side to improve security in the future – that if accounts are hacked into that the account owner cannot be used to send spam and to suffer financial damage
Many thanks to Yicheng Zhou and Abhijith Pillai for contributing to this blog